What is a data breach and how to prevent it?
The mobile software industry is no stranger to large-scale breaches. In the past few years, we have seen a lot of data breach incidents.
Guidus, a popular role-playing game on the Google Play Store, has breached much data about its vast user. It is a beautiful pixelated role-playing game, and players can choose to play different roles of heroes to find the adventure of the palace.
The app has been downloaded more than 100,000 times and has a 4.6-star rating based on 16,000 user reviews. After the incident, hackers could gain access to gamers' personal information, including their currency and game progress in-app. Even worse, they could delete that data and cause players to lose their progress. However, the developer did not make further optimization and improvement plans.
Data breaches are a serious problem that can lead to money loss, reputation damage, information loss, identity theft, and more. That's why it's essential to understand how it can happen and take steps to prevent it.
What is a data breach?
A data breach releases sensitive, confidential, or protected data into an untrusted environment, where people gain access to information they should not have. Information may be acquired in various ways, both accidental and deliberate. Data breaches are an often overlooked cyber hazard because someone can misuse them with even more severe consequences once a breach occurs.
Like the credit card you use to shop online, your credit card number, expiration date, and security code are all sensitive information. If this data is breached by someone who shouldn't have it, the criminal could use your credit card to make unauthorized purchases.
What's the difference between a data leak and a data breach?
Put simply, one is caused by external forces, and the other by internal forces.
External forces cause data breaches. Attackers use technology to overcome a series of security measures of network protection through planned network attacks.
Internal dynamics lead to data leakage. For example, if a leak occurs in the secure data center where the data is protected, there is a risk of accidental leakage of covered data.
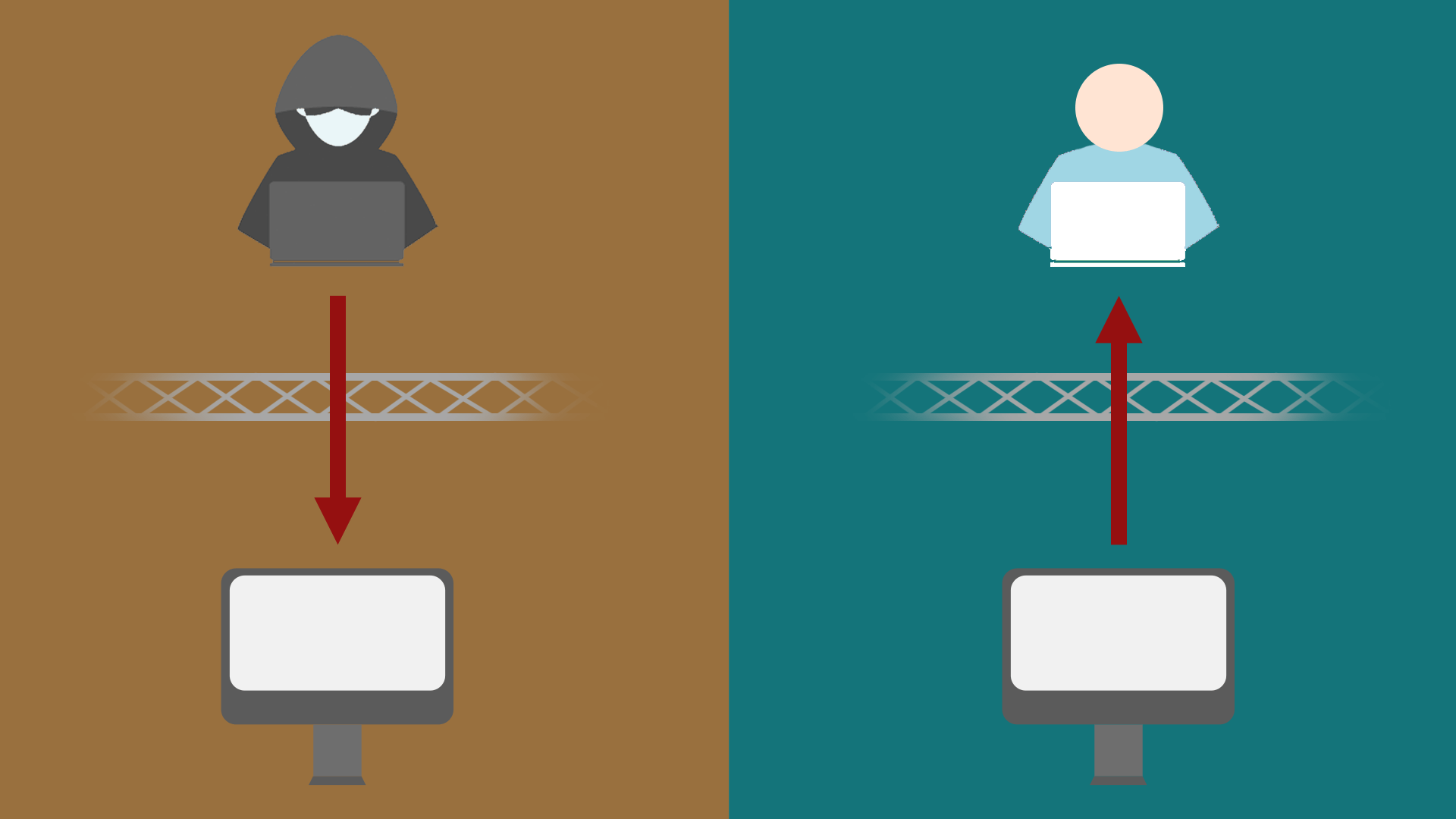
Data breach
A data breach is the result of a planned cyber attack. These events are triggered by external impetus. Cybercriminals must overcome a host of security measures protecting network data before they can detect sensitive data breaches from unauthorized users.
Data leak
A data leak is the accidental disclosure of sensitive information. These events were not triggered by external impetus. Instead, they are caused by breaches in the security control center that protects confidential data, flawed security policies, and poorly developed applications that leave personal information exposed and at risk. The key here is that data leak originates from the inner.
How data breaches happen?
Data breaches can occur in several ways:
Hacking: hacker gaining unauthorized access to a system or database. They can do this by using special software or exploiting security holes.
Accidental release: this is a case of the artificial avoidance of data. Someone deliberately releases sensitive information related to interests or core data related to business for personal or damage to the company's reputation.
System misconfiguration: IT engineers in an organization misconfigured a system, causing unpatched vulnerabilities in the system itself, which could expose data. Hackers can gain access if a system is not adequately protected.
What data be breached?
Major data breaches include data breaches involving personally identifiable information. For example, the personally identifiable information involved may consist of the following:
- Names
- Addresses / Email addresses
- Phone number
- Credit Card numbers
- passwords
- Browsing histories
- Interests and habits
Company data breaches can result from a malicious attack by a competitor or an employee deliberately publishing internal activities for personal gain. Company data breaches may include the following:
- Internal communications
- Company strategy
- Market layout
- Upcoming product plans
- Financial Information
- Proprietary technology information
How to prevent data breaches?
Train your security awareness
Security training is an integral part of improving your data security awareness from now on. However, sensitive data loss, compliance fines, and image loss, the impact of data breaches are all the same. To prevent this risk, focus on improving personal data protection security awareness.
Secure network perimeters: utilize security tools to deny unauthorized access and prevent attacks against information systems.
Vulnerability testing: regularly and systematically review the security weaknesses of the data center, simulate network attacks to check exploitable vulnerabilities, and repair them as soon as possible.
Keep your software up to date: outdated software is often the cause of data leaks. Be sure to update all programs to patch any security holes.
Use multi-factor authentication: multi-factor authentication adds an extra layer of security to your account. That means even if someone can guess your password, they will still need other information to access your account.
Monitor your accounts: regularly check your bank and credit card statements for unauthorized transactions.
Protect your sensitive data
Perhaps choosing a professional data protection tool can save more effort. Professional DLP (data loss prevention) provides professional data protection solutions. However, considering the balance of cost and utilization, more suggestions are suitable for enterprise-level data security protection, increasing the transparency of data usage and storage methods. So for individuals who cannot afford high professional service fees, what other ways can protect private data:
Use strong passwords: strong passwords are critical to keeping your data secure. Use a mix of letters, numbers, and special characters to create strong passwords.
Use a VPN: A VPN encrypts your internet traffic, making it harder for third parties to snoop on your online activities.
Be careful what you post online: What you share online. Avoid sharing sensitive information, such as your home address or financial information.
Watch out for phishing scams: Phishing scams are a common way hackers gain access to data. Be on the lookout for suspicious emails or websites trying to steal your information.
Follow Us on Social Media
Recent Articles
How to Use VPNs for Secure Social Media Management
Jul 29, 2024 | 9 mins to readHow to Set Up a VPN on Windows 10/11?
Aug 14, 2024 | 7 mins to readHow to Use Signal App in Russia: Solve Signal Ban
Aug 12, 2024 | 4 mins to read30 Best FMovies Alternatives in 2024 (Still Working)
Aug 12, 2024 | 14 mins to readAccess anything anywhere anonymously with X-VPN
24/7 one-one live chat support
Ultimate protection for 5 devices
Access to all worldwide contents
8000+ servers at 225 locations
30-DAY MONEY-BACK GUARANTEE

