30 Top VPN Features: How They Work?
VPN offers a range of features designed to enhance security, privacy, and internet freedom. But do you know the exact roles of these features? How do they work? And do you need to use them?
In this guide, we'll demystify 30 VPN features— from essential encryption techniques to useful device support for users' needs. By the end, you can confidently navigate the VPN landscape and find the perfect fit. Let’s dive in!

Security Features
VPN security features, which are crucial for a VPN, are designed to protect online data and ensure surfing activities remain private and secure.
1. AES-256 Encryption
2. SSL/TLS Encryption
3. Double VPN
4. Kill Switch
5. Leaks Protection
6. Onion Over VPN
7. Multi-Factor Authentication
8. Automatic Wi-Fi Protection
9. P2P Support and Protection
AES-256 Encryption
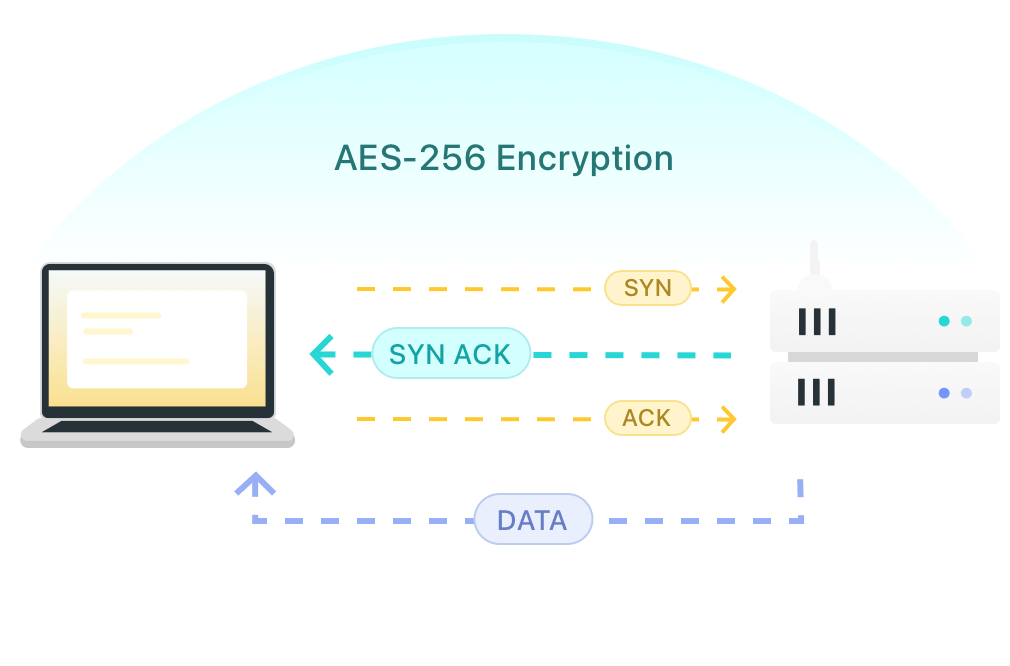
AES-256 encryption is a symmetric encryption standard widely used in reliable VPNs, like X-VPN. It centers on a high level of security by using a 256-bit key to encrypt and decrypt data, making it difficult to crack.
When you use a VPN to shop online or surf with public wifi, this technology encrypts all your data against many forms of cyber-attacks including DDoS attacks, phishing, and more.
For a deeper understanding of encryption, visit our What is a VPN page.
SSL/TLS Encryption
Secure Sockets Layer and Transport Layer Security are both Internet protocols for ensuring security in Internet communications. SSL/TLS encryption is built to secure online data transmitted by encrypting the connection between a browser and a web server.
This means that if you use a browser to log into any private account while connected to a VPN, sensitive info such as your login credentials and personal data will not be snooped or stolen by third parties.
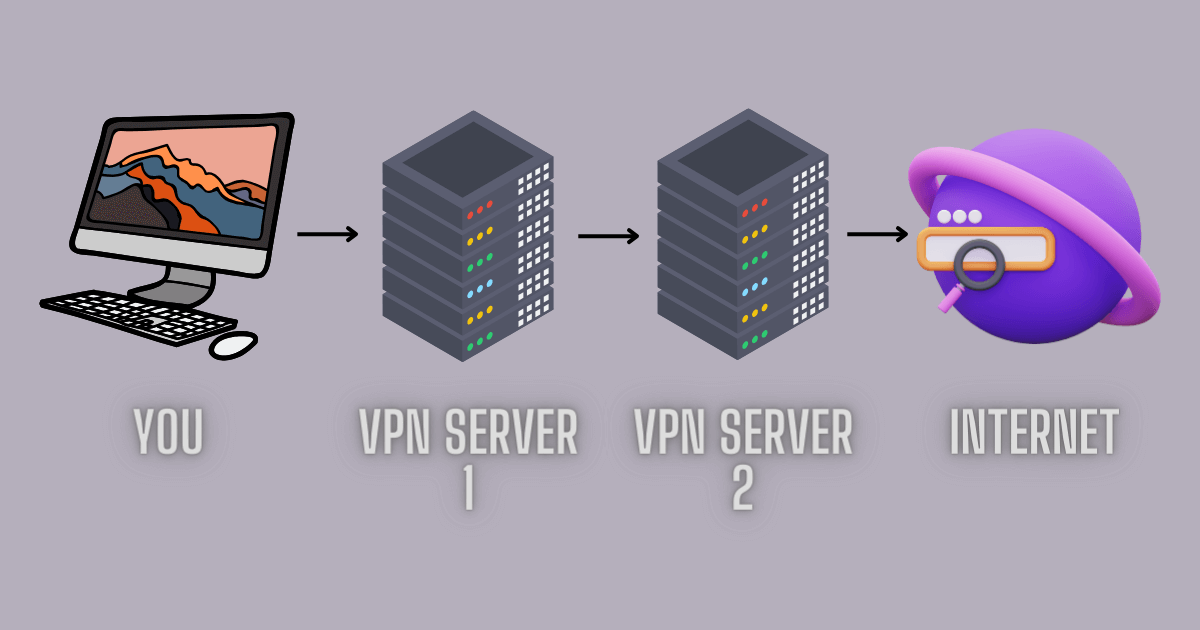
Double VPN
This feature means the VPN will route your online traffic through two servers instead of one, providing an extra layer of encryption for greater security.
Double VPN is ideal for users who require high-level data security to against surveillance and cyberattacks, such as journalists, activists, or anyone handling sensitive data.
Kill Switch
When the Kill Switch feature is turned on, your IP address will be frequently monitored by the VPN. If the VPN connection drops unexpectedly, your IP address changes immediately. Then Kill Switch, which monitors the situation, will automatically cut off your internet to prevent your real IP address and any data from being exposed, ensuring continuous security and anonymity while you are online.
Learn more about Kill Switch and its importance in our VPN Security Explained: Kill Switch, Split Tunneling, More page.
Leaks Protection
While using a VPN, sometimes your original IP address may get revealed, exposing your real geo-location, surfing footprints, and all online activities, due to IP leak, DNS leak, or WebRTC leak.
You can hit the button to download X-VPN to experience its built-in leak protection and start a VPN test to check whether the protective measure is in force.

Onion Over VPN
This VPN feature is one of the best assistants in preventing third-party monitoring and tracking. With Onion Over VPN, the online data will first be routed through a VPN server and then pass through the Tor network, thus gaining multiple layers of encryption and extremely strong security.

Multi-Factor Authentication
MFA in a VPN brings robust security by requiring multiple forms of verification before granting account or resource access. This typically involves a basic username - password and something else you have (like a code sent to your phone), ensuring only authorized users can connect to the VPN and reducing the cyber risk.
Automatic Wi-Fi Protection
The Auto Wi-Fi Protection feature will automatically connect to a VPN server when you connect your device to an unknown Wi-Fi network and encrypt data immediately. For users who often work or study in public places, this feature proactively creates a strong security shield for personal data in public network environments to effectively combat any criminal attempt by unscrupulous individuals.

P2P Support and Protection
P2P ( peer-to-peer) sharing, also torrenting, requires users to download a file via the BitTorrent network, which may lead to cyber risks by exposing your IP address. The P2P Support and Protection in a VPN for torrenting will ensure that your IP address is hidden, encrypt data to prevent monitoring and protect against ISP throttling.
Privacy Features
Privacy features in a VPN use a variety of tricks to get you to wear the Harry Potter Invisibility cloak, hiding from the tracking and prying eyes of any hacker or third-party organization.
10. Hide IP Address
11. No-log Privacy
12. RAM-Only Servers
13. Private Browser
14. Private DNS
Hide IP Address
VPNs can hide IP addresses by routing internet traffic through a server worldwide, which will give you a mask and a cape to pretend you’re surfing from the server’s location.
This is the core function of VPNs, in addition to protecting your identity and preventing tracking, it also can help people bypass the geo-restrictions to access all streaming and other content no matter where you actually are.
For more details on how VPNs protect your identity, see our How VPNs Protect Your Privacy and Online Identity page.
No-log Privacy
The No-Log Policy is a privacy commitment that VPN providers, such as X-VPN and other trusted services, make to their users. They pledge never to log your online activities, VPN usage times, or real IP addresses in any form, nor to store or sell your private data.
Hence, selecting a VPN that strictly adheres to this No-Log Policy and has a clean record free of data leaks is essential for safeguarding your privacy.
Check out our What is a VPN page to understand the importance of a no-log policy.
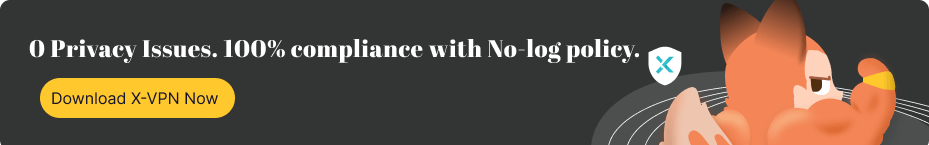
RAM-Only Servers
Most providers will rely on hard disks to run their services. User data will remain stored on the hard disk until it is overwritten by new data - which obviously leaves a significant risk to user privacy.
Therefore, top services like ExpressVPN use RAM-only servers to add credibility to their No-log policy promises. RAM servers require constant power to retain information, and all data is wiped out in the event of a power failure and reboot, ensuring that no user data can be stored long-term.
Private Browser
A private browser is a feature that only a few leading VPNs will offer. It is essentially a web browser with a higher level of privacy and security, usually built into the VPN client or app. When users surf the web through a private browser, it blocks third-party cookies, disables history, encrypts private data, and minimizes your activity footprint to improve your online privacy.

Private Browser of X-VPN
Private DNS
Generally, we usually use public DNS services provided by ISPs, but these DNS servers make ISPs log everything we do online. Private DNS in a VPN, on the other hand, is a user-specific and secure DNS server.
The VPN handles DNS requests internally and ensures that your browsing activities are kept confidential to the ISP as well as to any third parties, effectively reducing the risk of data leakage and preventing potential data surveillance.
Performance
The performance features of a VPN are the aspects that shape its quality of service, reliability, availability, and functionality. They directly determine whether a VPN product is competitive in the marketplace.
15. Servers and Locations
16. Speed
17. VPN Protocols
18. Smart Routing System
19. Split Tunneling
20. Stealth Mode
21. Obfuscation
22. Dedicated Server
23. Dedicated IP Addresses
24. Static IP
25. Smart DNS
26. Data Compression
27. Shortcut
28. Security Tools
Servers and Locations
The servers and locations of a VPN are the physical and virtual servers set up by the provider in various regions worldwide. These servers route user traffic to their locations, enhancing network speeds, accessing geo-restricted content, hiding IP addresses, and preventing server congestion.
A broad range of servers and locations showcases the VPN's strength - X-VPN offers over 8,000 servers in 225+ locations, click the link to check out its vast network support.
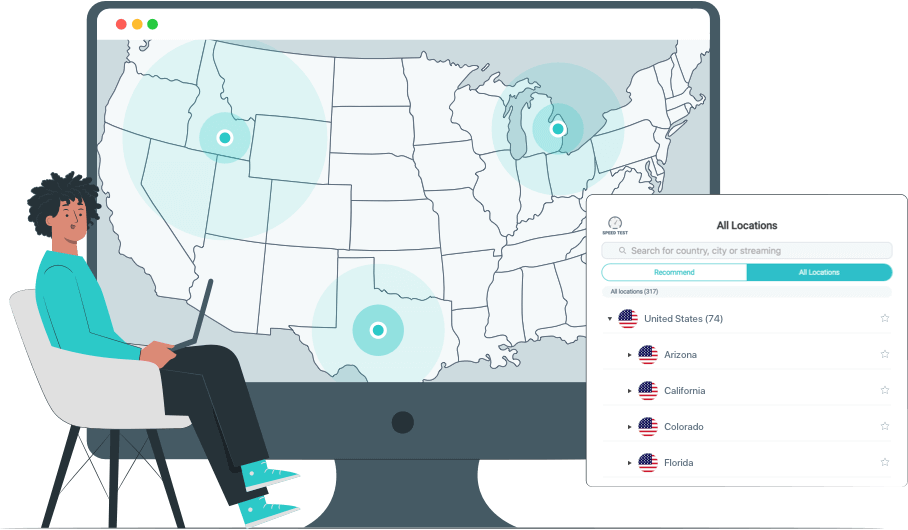
Speed
VPN speed is measured by download speed, upload speed, and latency. Factors like server proximity, server capacity, encryption level, VPN protocol, network conditions, and device performance will impact this speed, resulting in some speed loss.
A top-tier VPN should offer speeds close to the user's base internet speed for low-latency performance. For instance, X-VPN limits speed loss to no more than 15%, ensuring a smooth and fast online experience.
Speed Test of Using X-VPN Results by speedtest.com
VPN Protocols
VPN protocols dictate how data is transmitted and encrypted, impacting the speed, security, and reliability of a VPN. Common protocols include OpenVPN, WireGuard, and L2TP/IPSec, each suited for different use-case scenarios.
A strong VPN should support multiple protocols to meet the different needs of users. For example, OpenVPN offers robust security and stability, ideal for general use. WireGuard provides high-speed performance for fast browsing. Some providers, like X-VPN, even develop proprietary protocols like Everest to enhance their service.
VPN Protocols Support of X-VPN
Smart Routing System
The physical distance between the user and the connected VPN server can affect VPN speed - the closer, the faster. No need to guess the distance yourself, a Smart Routing System can identify the fastest and most stable VPN server based on your real geo-location and current network status.
Simply click the Quick Connect button on the VPN homepage, and the system will automatically connect you to the best server in seconds.
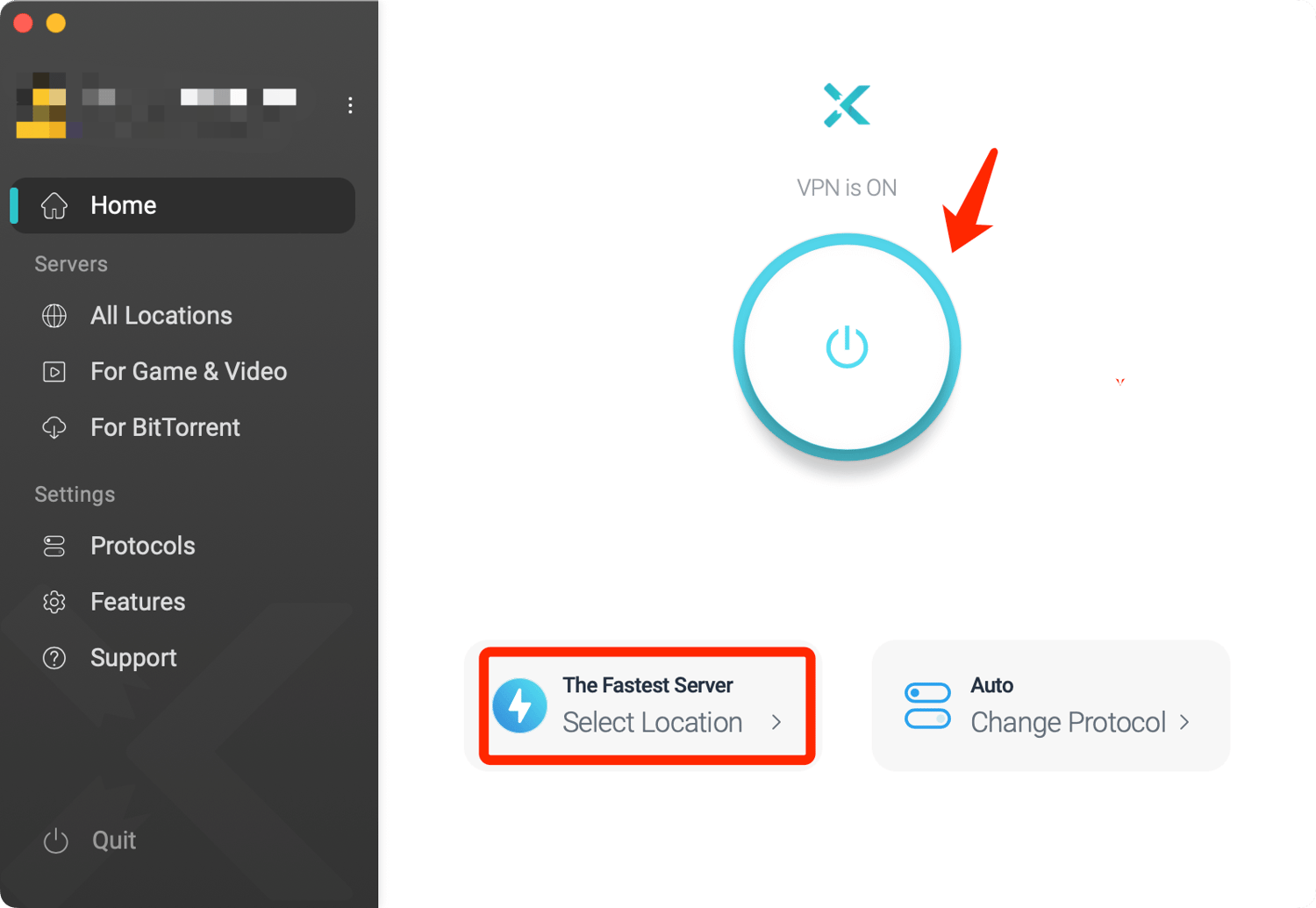
X-VPN Smart Routing System
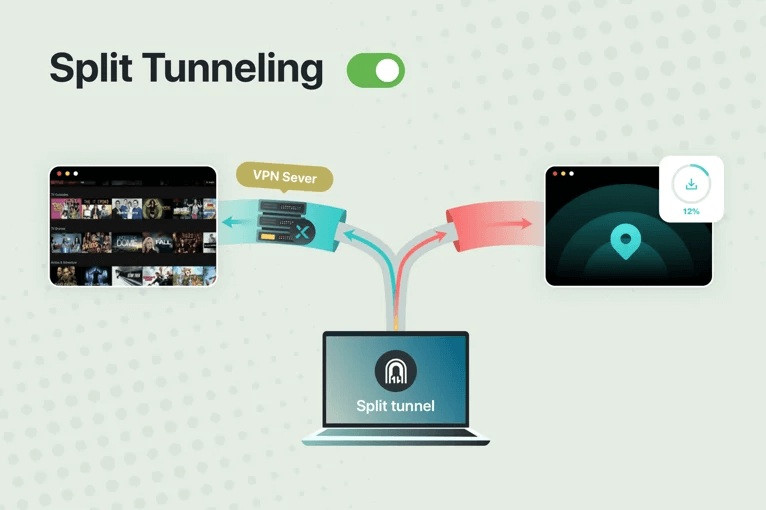
Split Tunneling
Split Tunneling, typically available in VPN Premium plans, allows users to choose which applications route through the VPN and which access the internet directly. This VPN feature greatly enhances the flexibility of VPN usage. For example, you can perform high-speed local download tasks while accessing global streaming libraries via the VPN.
By using Split Tunneling, you can optimize your internet experience, balance VPN security and availability, reduce bandwidth usage, and increase network efficiency.
Stealth Mode
The stealth mode of a VPN is able to bypass Deep Packet Inspection and other forms of network monitoring by various websites or platforms to help users successfully access restricted content.
The primary purpose of this feature is to disguise VPN traffic so that ISPs or network administrators would think that the user's traffic has nothing wrong as usual to evade VPN detectives.
Obfuscation
Obfuscation is a technique employed by Stealth Mode to disguise VPN traffic as regular internet traffic. It plays a big role when users deal with strict internet censorship and regional restrictions. Essentially, Stealth Mode is a user-facing VPN feature, while obfuscation is the underlying tech it uses to achieve its goal.
But different VPN providers may integrate obfuscation in various ways - they might provide obfuscated servers or proprietary protocols with built-in obfuscation.

Dedicated Server
Dedicated servers in a VPN are servers that are dedicated to a user or organization to ensure better performance, enhanced security, and custom configuration options.
These optimized servers are great for businesses that need secure remote access to the company network or professional web developers and are also ideal for watching high-bandwidth streaming media and lowing game pings.
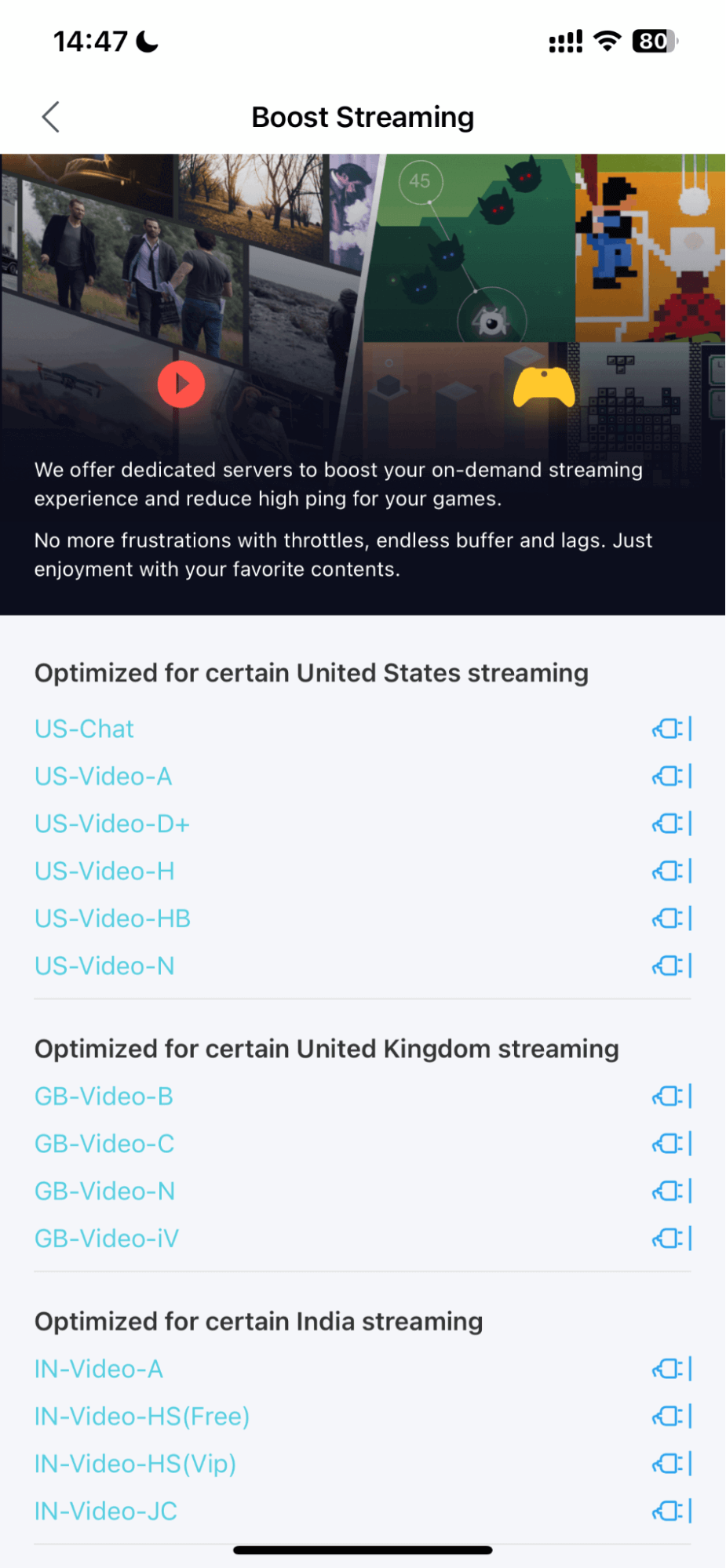
The Dedicated Servers of X-VPN
Dedicated IP Addresses
A dedicated IP address is assigned exclusively to a single user without sharing with other users, ensuring a consistent online identity and reducing network regulators' suspicions about VPN traffic.
While it doesn't significantly boost VPN performance like dedicated servers do, it enhances VPN security and reliability, making it shine for accessing secure networks such as online banking and official platforms.
Static IP
A static IP is a constant IP address assigned by a VPN provider, giving your device a fixed network identity. It aids in bypassing VPN detections and is crucial for seamless remote work, stable access to security systems, and remote desktops due to its reliability and geographic consistency.
While static IPs and dedicated IPs are very similar in their roles, dedicated IPs are only assigned to one user, while static IPs can be shared. Currently, all these 2 functions are only available to premium VPN users, click the button below to get more info.

Smart DNS
Smart DNS is a tech that unlocks geo-restrictions through DNS Query Redirection for VPN. When you visit a website, your device originally sends a DNS query to change the domain name into its IP address. When you enable Smart DNS, the DNS queries are blocked and rerouted by proxy servers located in different regions.
Because it routes only DNS-related traffic, Smart DNS maintains faster speeds compared to normal VPN services and keeps your original IP address to access the global streaming platforms easily.
Data Compression
Using data compression significantly reduces the amount of data that needs to be routed through the VPN, thus minimizing bandwidth usage. The lesser amount of data will also decrease the time it takes to encrypt and transfer data, improving the VPN speed and performance.
For those who use mobile web surfing, the data compression feature will be good for your wallet.
Shortcut
VPN Shortcut allows users to create a Shortcut on the device's desktop/home screen. Clicking on its icon, users can quickly connect to the VPN service, simplifying and speeding up the connection process.
This feature ensures that your device is secured in the shortest time, reducing browsing risks and facilitating access to global content. For users who rely on a VPN for their work or streaming fans, Shortcut will undoubtedly make their online experience better.
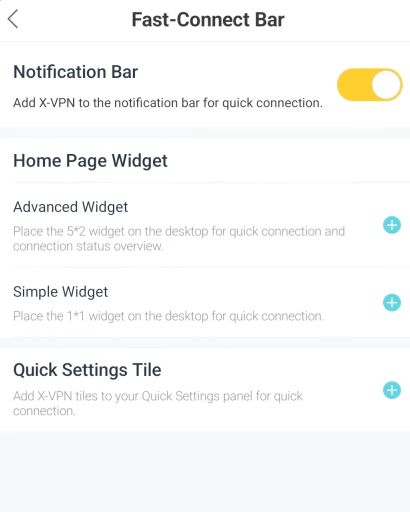
Shortcut Feature in X-VPN
Security Tools
Security tools for a VPN include various testing and verification tools offered by the provider to ensure its service is functioning correctly and securely and also help its users build a safer surfing environment.
Use X-VPN as an example, it has these Security tools below.
・DNS Leak Test: Check whether the DNS queries are leaking.
・IPv6 Leak Test: Verifies that your real IP address is hidden and not exposed.
・WebRTC Leak Test: Ensures your browser does not reveal your real IP address.
・IP Address Checker: Check your real IP address.
・IP Address Lookup: Check the state, geo-location, and details of any IP address.
・Password Generator: Create strong and complex passwords for free.
Device Support
In addition to the features above that highlight a VPN's capabilities, a provider's support for its customers and their devices will also determine whether it is widely available.
29. Compatibility
30. Simultaneous Connection
Compatibility
When choosing a VPN, compatibility is a crucial factor to consider. It determines the ability of a VPN service to work across different devices, operating systems, and apps.
Strong compatibility is vital for comprehensive online security and convenience. It ensures that users can establish a secure VPN connection on all their devices, allowing them to enjoy VPN features seamlessly across various platforms.
For now, X-VPN supports a wide range of platforms, including Windows, macOS, Linux, Android, iOS, Chromebook, Chrome extensions, routers, game consoles, and smart TVs. You can hit the icon to get a VPN download according to each device.

Simultaneous Connection
Simultaneous connection lets you secure multiple devices with only one single account. Imagine enjoying all VPN features on your PC, smartphone, tablet, or smart TV, and even setting up an Xbox VPN at the same time—no extra accounts needed.
However, you can also get unlimited connections by setting a VPN for router - all devices connected to that router will be under VPN protection.
Conclusion
Learning VPN features can help you further evaluate and determine if a VPN service is worthwhile and well-marketed.
After reading through our blog, if you want to use these 30 VPN features to create a safer, faster, and more comfortable surfing environment for yourself, click the button below to get X-VPN for free and check out the specific guide on how to use a VPN.

FAQs
What are the features of a VPN?
Relying on standard encryption technologies, Double VPN, Kill Switch, MFA, and other security functions, VPNs can build a robust shield to keep you safe from various cyber risks. Hiding IP addresses with a no-log policy, a VPN can clean your online footprints to safeguard your privacy. Meanwhile, performance features like Split tunneling, Static IP, Obfuscation, etc., and device support also help users unblock geo-limitations, reduce game latency, and provide a seamless, unrestricted internet experience.
What features and advantages can a VPN connection provide?
A VPN connection can provide a secure but colorful online experience by encrypting data, hiding your IP, and unlocking geo-restricted content. In other words, you can use it to ensure your online privacy, clean risks on public Wi-Fi, bypass censorship, and also reduce gaming lag.
Follow Us on Social Media
Recent Articles
How to Use VPNs for Secure Social Media Management
Jul 29, 2024 | 9 mins to readHow to Set Up a VPN on Windows 10/11?
Aug 14, 2024 | 7 mins to readHow to Use Signal App in Russia: Solve Signal Ban
Aug 12, 2024 | 4 mins to read30 Best FMovies Alternatives in 2024 (Still Working)
Aug 12, 2024 | 14 mins to readAccess anything anywhere anonymously with X-VPN
24/7 one-one live chat support
Ultimate protection for 5 devices
Access to all worldwide contents
8000+ servers at 225 locations
30-DAY MONEY-BACK GUARANTEE

