What is a VPN tunnel and how it works?

What is a VPN tunnel?
First, we can imagine a tunnel, and why are there tunnels?
In the real world, tunnels are usually used to cross or connect uncrossable terrain. For example, a mountain separates the road from city A to city B. Tunnels are an efficient solution to connect A and B.
In the online world, a VPN tunnel is an encrypted connection between your device, such as a computer, smartphone, or tablet, and a VPN server. It is an efficient and secure connection between networks.
How do VPN tunnels work?
VPN tunnel is a data packaging technology that encapsulates the original IP packet in another packet to send and receive data. It hides your IP address and encrypts the data you transmit over the Internet and the data you generate while surfing the web. Snoopers won't be able to access your online data or track your activity because the data you transmit is encrypted in the tunnel, making it impossible to crack the connection without the decryption key. The tunnel will not damage your private data and will make your data more secure and confidential cause the encryption during tunneling.
So, what is the protocol?
In computer science, a protocol is an agreement or call rule designed by the two parties to realize the communication. Just like human languages, in addition to the world's largest lingua English, there are thousands of other languages, such as French, German, Chinese, Arabic, Spanish, etc. also local dialects in different regions. It is because so many language types are for more convenient and efficient communication between human beings.
A protocol is the language of computers. It tells computers how to talk to each other. For example, if necessary to obtain a web page, what form should be used to send it? What form should be used to receive it? And what format should be used to give feedback? These are all rules of protocol. It is worth mentioning that although humans determine the rules of the protocol, they are highly normative. An error will appear if a particular symbol is misused during use.
How does the tunneling protocol encrypt?
Many different VPN tunneling protocols vary in speed, level of security, encryption process, and other features. Common VPN tunneling protocols include PPTP, SSTP, L2TP, OpenVPN, etc. In addition, different protocols use different encryption methods. Taking TCP as an example, the transmitted data is encrypted by a three-way handshake and four-way wave.
How to use a VPN tunnel?
Generally, you do not need to set anything. X-VPN completes all configurations for you. In addition, X-VPN will automatically match the best protocol and server with just a one-click connection if you were using the X-VPN service or downloaded the X-VPN application.
What can I do with an encrypted tunnel?
When connecting to a VPN tunnel, your security is fully protected. Otherwise, all your data will be exposed without a VPN.
- Your traffic is encrypted and cannot be read by third parties.
- Your IP address is hidden, and your online data is passed through a VPN server which hides your IP address and, thus, your actual location.
- Safer under public Wi-Fi, after successfully connecting to VPN, the secure tunnel can prevent your data from being stolen by people using the same network without worrying about being tracked, monitored, or data intercepted.
- Bypass the government's blockade and browse the global news at will.
- Prevent ISPs from monitoring and tracking your Internet behavior, view and log your online activities, and avoid obtaining your IP address and location through the websites you visit.
- Prevent hackers from stealing personal data, and avoid using improper means to obtain your privacy security data, malware, phishing, and DDoS attacks to intercept data.
What is split tunneling?
A VPN tunnel encrypts all of your traffic, but you may not want this in some cases. Especially when you need to switch between different applications to complete work, study, or entertainment simultaneously, choosing which applications need VPN protection and which do not is the function of split tunneling.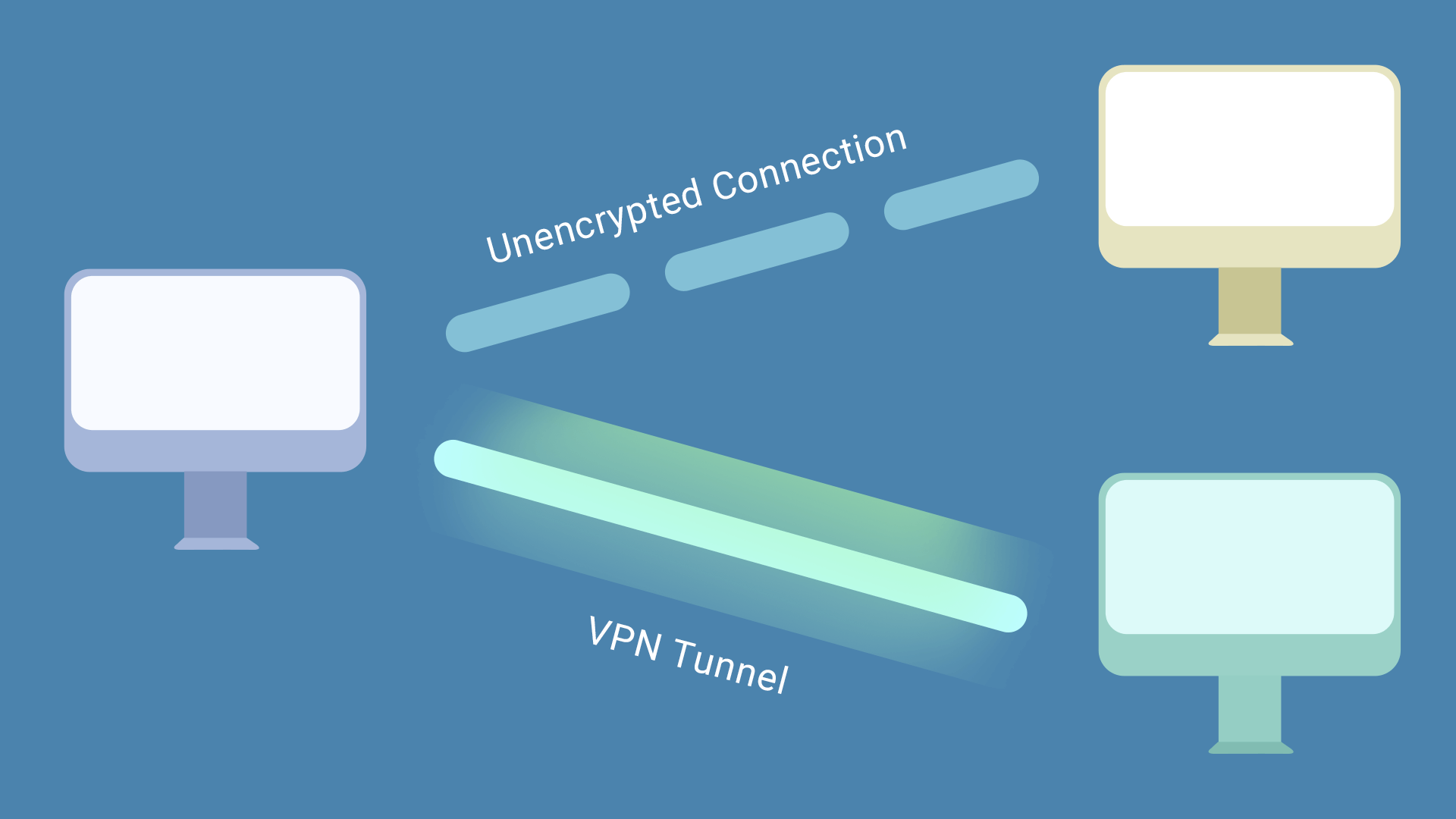 Why is split tunneling necessary?
Why is split tunneling necessary?
Split tunneling is an advanced VPN feature that allows you to divide your internet traffic by encrypting some of it and sending it through a secure VPN server while allowing the rest to travel directly on the Internet. Split tunneling can protect partial traffic encryption while maintaining access to local network devices, satisfying free switching between private and public networks, and transmitting data over faster, unencrypted, open networks.
You may need to use a VPN to bypass geographical restrictions and enjoy the weekend time of the latest movies and TV shows on Netflix. You may also receive a pending Gmail and feel smooth when replying to emails without a VPN.
How to use split tunneling?
The local network environment sometimes affects redirecting to a VPN server. Caton, disconnection, and speed reduction are all possible. No one can guarantee that the connection will always be 100% stable and fast. When you use a VPN, all your internet traffic is encrypted, and every piece of data is sent and received through secure servers. On the other hand, split tunneling gives you more control over what data is sent through your VPN server. It relieves traffic pressure to increase Internet speed.
You can use split tunneling on Android and Windows only. iOS and macOS do not support split tunneling.
Step 1 Open X-VPN and click Advanced Features in the lower right corner.
Step 2 Select the Split Tunneling feature.
Step 3 Select the Settings placed under the Application Control.
Step 4 Click Add to enter the app list and select the app that needs to split up.
Step 5 Return to the main page and complete the settings.
Follow Us on Social Media
Recent Articles
How to Use VPNs for Secure Social Media Management
Jul 29, 2024 | 9 mins to readHow to Set Up a VPN on Windows 10/11?
Aug 14, 2024 | 7 mins to readHow to Use Signal App in Russia: Solve Signal Ban
Aug 12, 2024 | 4 mins to read30 Best FMovies Alternatives in 2024 (Still Working)
Aug 12, 2024 | 14 mins to readAccess anything anywhere anonymously with X-VPN
24/7 one-one live chat support
Ultimate protection for 5 devices
Access to all worldwide contents
8000+ servers at 225 locations
30-DAY MONEY-BACK GUARANTEE

