VPN Security Explained: Kill Switch, Split Tunneling, More

Why learn about VPN security features? Imagine managing your finances online when suddenly, your VPN disconnects, exposing your real IP, or you’re switching off your VPN for certain apps, risking your personal data without even realizing it. Features like a Kill Switch and Split Tunneling are built to protect you in these scenarios—ensuring your privacy without sacrificing convenience. This guide simplifies these crucial tools, empowering you to browse, shop, and stream with greater confidence and security.
Importance of VPN Security Features
Everyday activities like checking email, shopping, or streaming involve transmitting personal data that can be intercepted. VPNs encrypt this data, making it unreadable to hackers and ensuring your privacy. VPNs also hide your real IP address, preventing websites, advertisers, and even your ISP from tracking your online activities.
Key VPN Security Features Explained
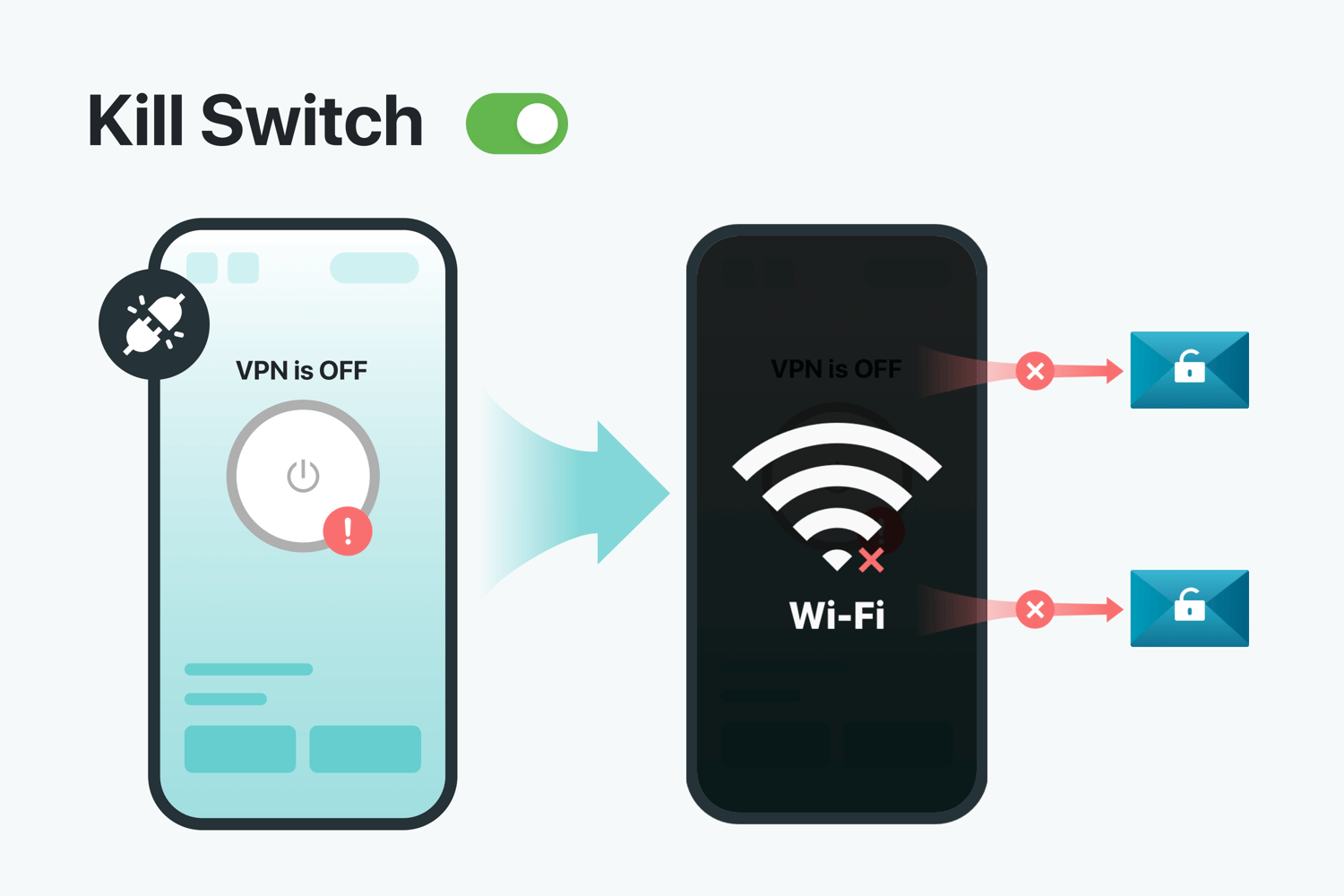
Kill Switch
Definition: A Kill Switch automatically disconnects your device from the internet if your VPN connection drops.
Importance: Without a Kill Switch, a failed VPN connection can expose your real IP address, making your online activities visible to your ISP or hackers. This feature is crucial for protecting sensitive activities like online banking or handling confidential work documents.
Usage Scenario: If you’re banking online and your VPN connection drops without a Kill Switch, your real IP is exposed, and sensitive banking information could be intercepted. A Kill Switch prevents this by cutting off your internet connection until the VPN is re-established.
For more on VPN basics, visit our What is a VPN page.
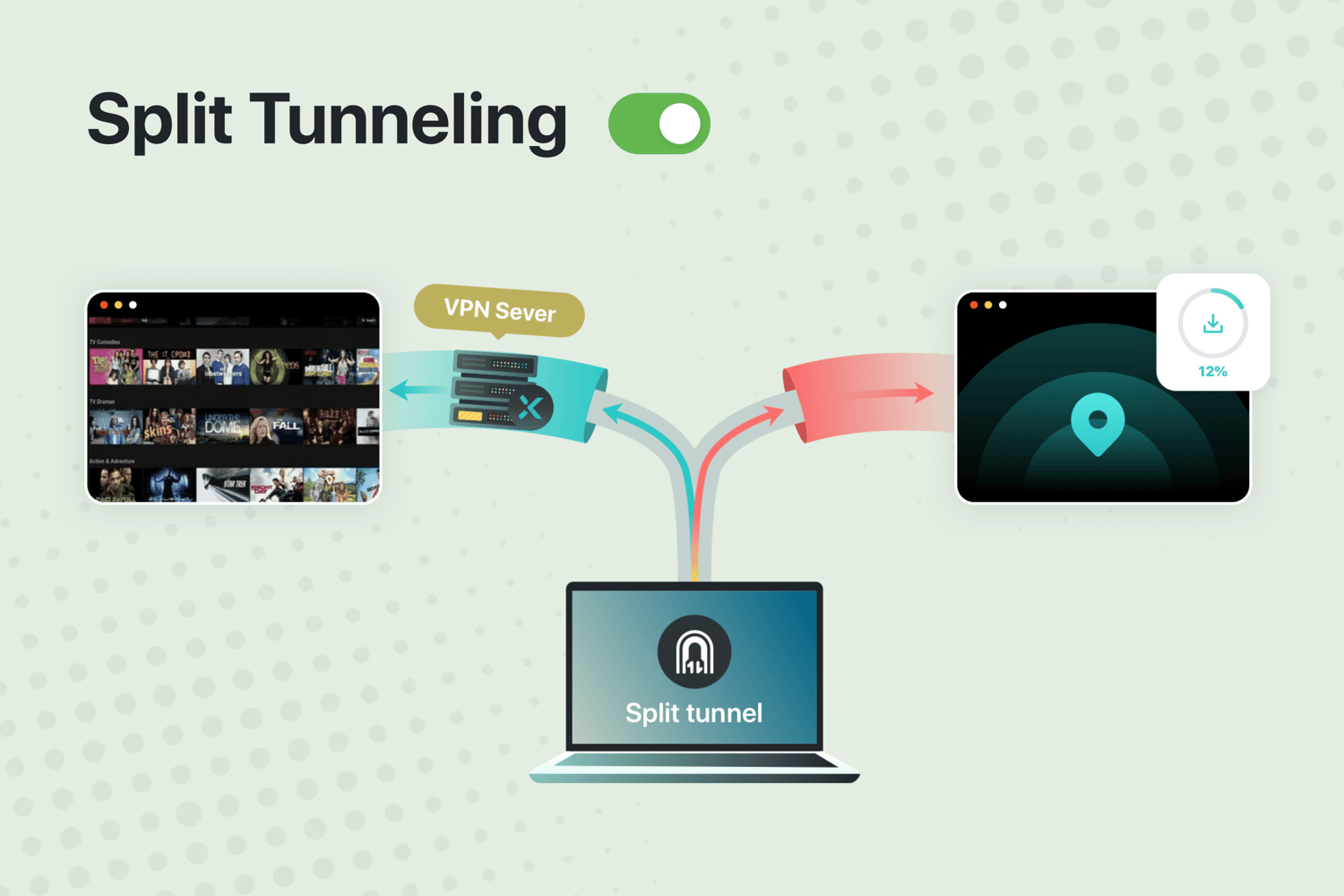
Split Tunneling
Definition: Split Tunneling allows you to choose which apps use the VPN and which connect directly to the internet.
Importance: This feature provides flexibility and can improve performance. For example, you can stream local content with your regular internet connection while keeping your online banking secure through the VPN.
Usage Scenario: You’re working on a research project and need fast access to local resources while keeping your personal data secure. Split Tunneling directs your research traffic through your regular connection for speed, while protecting your personal data via the VPN.
Learn about configuring Split Tunneling in our VPN Setup Guide.
AES-256 Encryption
Definition: AES-256 Encryption is a standard for securing data using a 256-bit key.
Importance: High encryption standards like AES-256 ensure that your data is secure and unreadable to anyone who intercepts it. It is widely regarded as virtually uncrackable.
Usage Scenario: When you send an email or make an online purchase, AES-256 encryption ensures your personal data is safe from hackers.
SSL/TLS Encryption
Definition: SSL (Secure Sockets Layer) and TLS (Transport Layer Security) are protocols that encrypt data as it travels over the internet.
Importance: These protocols secure your data during transmission, making it unreadable to eavesdroppers.
Usage Scenario: SSL/TLS encryption protects your data when you visit websites with “https” in the URL.
No-Log Policy
Definition: A No-Log Policy means the VPN provider does not keep any records of your browsing history.
Importance: This ensures that even if the VPN provider is asked to hand over user data, they have nothing to provide. It is crucial for maintaining your privacy.
Usage Scenario: If you’re using a VPN for sensitive activities, knowing that your provider doesn’t keep logs gives you peace of mind.
DNS Leak Protection
Definition: DNS Leak Protection prevents your DNS queries from being exposed outside the VPN tunnel.
Importance: Without this protection, your ISP could see the websites you visit, even if your VPN connection appears secure.
Usage Scenario: When visiting sensitive or private websites, DNS Leak Protection ensures your activity remains confidential. You can perform a DNS leak test to check your protection.
Server Obfuscation
Definition: Server Obfuscation disguises VPN traffic to make it look like regular internet traffic.
Importance: This helps bypass VPN blocks and censorship in restrictive environments.
Usage Scenario: When traveling to countries with strict internet censorship, server obfuscation ensures you can still access blocked websites.
Double VPN
Definition: Double VPN routes your traffic through two VPN servers, doubling the encryption.
Importance: This feature provides an extra layer of security and anonymity.
Usage Scenario: When performing highly sensitive tasks, double VPN ensures maximum privacy.
Onion Over VPN
Definition: Onion Over VPN combines the anonymity of the Tor network with the security of a VPN.
Importance: This provides multiple layers of encryption and anonymity.
Usage Scenario: When accessing the dark web or requiring maximum anonymity, Onion Over VPN ensures your activities are untraceable.
Automatic Wi-Fi Protection
Definition: Automatic Wi-Fi Protection automatically connects your device to a VPN when it joins an unsecured Wi-Fi network.
Importance: This ensures your data is always protected on public Wi-Fi.
Usage Scenario: When you connect to public Wi-Fi at a café, automatic Wi-Fi protection ensures your data is immediately secured.
P2P Support and Protection
Definition: P2P Support and Protection allow safe and anonymous file sharing over peer-to-peer networks.
Importance: This protects your data and identity when using P2P networks.
Usage Scenario: When downloading files via BitTorrent, P2P protection ensures your IP address remains hidden.
Secure VPN Protocols
Definition: VPN protocols like OpenVPN, WireGuard, and IKEv2/IPsec determine how data is transmitted over a VPN.
Importance: Secure protocols ensure reliable and safe data transmission.
Usage Scenario: When choosing a VPN, opting for one that supports secure protocols like OpenVPN ensures your data is transmitted securely.
For more information on VPN protocols, see our article on Understanding VPN Protocols: How They Impact Your Online Security and Speed.
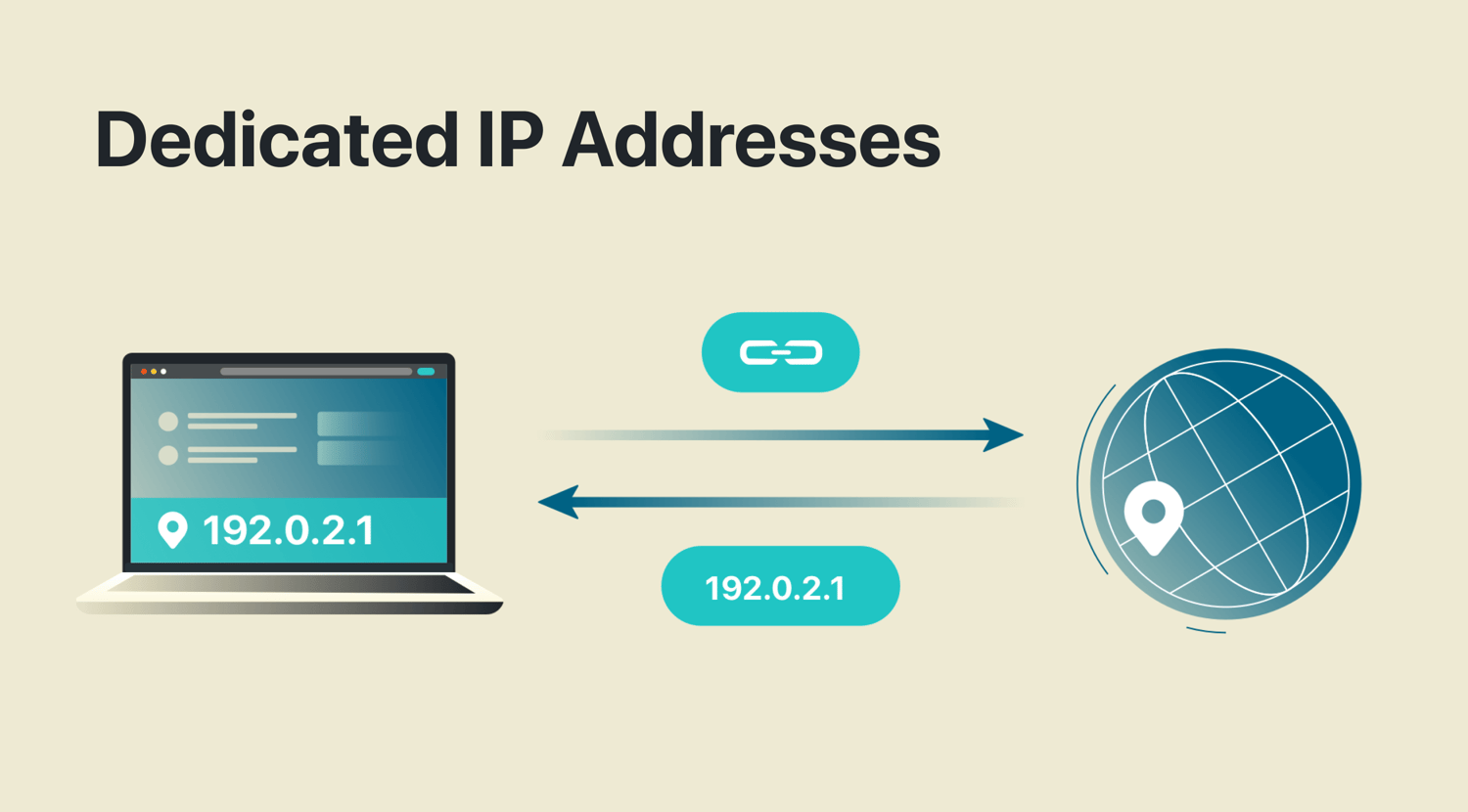
Dedicated IP Addresses
Definition: Dedicated IP Addresses provide a unique IP address exclusively for your use.
Importance: This can help avoid IP blacklists and reduce the risk of CAPTCHAs.
Usage Scenario: When accessing sensitive accounts or services, a dedicated IP address ensures consistent access.
IPv6 Leak Protection
Definition: IPv6 Leak Protection prevents your IPv6 address from being exposed.
Importance: This ensures complete anonymity and prevents data leaks.
Usage Scenario: When using a VPN, IPv6 leak protection ensures all traffic, including IPv6, is routed through the VPN.
Stealth Mode
Definition: Stealth Mode disguises VPN traffic to evade detection and bypass firewalls.
Importance: This is essential for bypassing internet censorship.
Usage Scenario: When accessing restricted content in countries with heavy internet censorship, stealth mode ensures your VPN traffic remains undetected.
Data Compression
Definition: Data Compression reduces the amount of data sent over the VPN, improving speeds and reducing bandwidth usage.
Importance: This can improve performance, especially on slower connections.
Usage Scenario: When using a VPN on a mobile network, data compression ensures faster speeds and reduced data usage.
Who Needs These Features?
Frequent Travelers
Relevance: A VPN with features like Kill Switch, Split Tunneling, and Server Obfuscation is essential for travelers. It protects your data on public Wi-Fi networks and allows you to access content as if you were back home, bypassing geographical restrictions.
Example: Business travelers can securely access company emails and sensitive documents using a VPN, while streaming local news and entertainment through a direct connection for better speed.
Remote Workers
Relevance: Remote workers need secure access to company networks and sensitive information. Features like a Kill Switch, Secure VPN Protocols, and P2P Support ensure your connection remains private and efficient.
Example: A remote worker can use Split Tunneling to ensure work applications are secured through the VPN, while personal browsing and streaming are done through a regular connection to save bandwidth.
Privacy-Conscious Users
Relevance: Anyone concerned about their online privacy will benefit from features like No-Log Policy, Double VPN, and Onion Over VPN. These provide multiple layers of security and anonymity.
Example: Privacy-conscious users can route all their sensitive activities like banking and email through the VPN, while using their regular connection for streaming and social media.
How These Features Relate to Daily VPN Usage
Protecting Sensitive Transactions
Relevance: Whenever you’re making online purchases or managing your finances, features like AES-256 Encryption, Kill Switch, and DNS Leak Protection safeguard your personal data.
Example: While buying groceries online, a Kill Switch ensures your payment details remain secure even if the VPN connection drops.
Streaming and Browsing
Relevance: Using a VPN to stream geo-restricted content or browse privately is common. Features like Split Tunneling and Stealth Mode can enhance your experience by routing only certain traffic through the VPN and evading detection.
Example: Students can use Split Tunneling to access university resources securely while streaming lectures on a faster direct connection.
Everyday Internet Use
Relevance: For general browsing, shopping, and social media, features like Automatic Wi-Fi Protection, IPv6 Leak Protection, and Data Compression ensure your data remains private and secure, providing peace of mind in your daily digital life.
Tips for Choosing and Setting Up Your VPN
Choosing the Right VPN
- Encryption Quality: Opt for VPNs that offer AES-256 encryption and reliable protocols like OpenVPN or WireGuard.
- Privacy Policies: Choose a VPN with a strict no-logs policy and transparent privacy practices.
- Server Diversity: Look for VPNs with a wide range of server locations to maintain fast and stable connections.
- Reputation and Reviews: Read user reviews and expert opinions to gauge the effectiveness and reliability of the VPN service.
- Customer Support: Ensure the VPN provider offers responsive and helpful customer support.
Setting Up Your VPN
- Step-by-Step Guide: Providing step-by-step instructions or a simple guide on setting up a VPN can make it easier for less tech-savvy users to get started.
- Configuration Tips: Include tips on configuring VPN settings for optimal security and performance, especially for remote workers.
- Device Compatibility: Share how to set up VPNs on various devices, including laptops, smartphones, and tablets.
For a detailed setup guide, check out our article on Quick Guide: Setup, Cancel, and Disable Your VPN
Conclusion
Understanding and utilizing VPN security features like Kill Switch, Split Tunneling, and others such as AES-256 Encryption, SSL/TLS Encryption, No-Log Policy, DNS Leak Protection, Server Obfuscation, Double VPN, Onion Over VPN, Automatic Wi-Fi Protection, P2P Support and Protection, Secure VPN Protocols, Dedicated IP Addresses, IPv6 Leak Protection, Stealth Mode, and Data Compression is crucial for maintaining your online privacy and security. Whether you’re a frequent traveler, remote worker, or just someone who values their privacy, these tools help you navigate the digital world safely. By choosing a VPN with robust security features, you can protect your personal data and enjoy a secure, convenient online experience.
For more information about what a VPN is and how it works, check out this detailed guide about what is VPN. If you’re ready to get started, you can download our FREE VPN app here.
FAQ
What if My VPN Connection Drops?
With a Kill Switch enabled, your internet connection will be automatically disconnected to prevent data exposure.
Will a VPN Slow Down My Internet?
While a VPN can affect speed, Split Tunneling allows you to choose which traffic goes through the VPN, optimizing performance for important activities.
Follow Us on Social Media
Recent Articles
How to Use VPNs for Secure Social Media Management
Jul 29, 2024 | 9 mins to readHow to Set Up a VPN on Windows 10/11?
Aug 14, 2024 | 7 mins to readHow to Use Signal App in Russia: Solve Signal Ban
Aug 12, 2024 | 4 mins to read30 Best FMovies Alternatives in 2024 (Still Working)
Aug 12, 2024 | 14 mins to readAccess anything anywhere anonymously with X-VPN
24/7 one-one live chat support
Ultimate protection for 5 devices
Access to all worldwide contents
8000+ servers at 225 locations
30-DAY MONEY-BACK GUARANTEE

