VPN Encryption: How It Works?
VPN Encryption is an important part of VPN functioning, ensuring that your internet data is protected from hacking, snooping, and interception.
To gain a deeper understanding of VPN encryption, including its workings and benefits, read this blog. We will offer a comprehensive guide that breaks down the complexities into easy-to-understand language.

What Is VPN Encryption?
VPN encryption usually starts by using the TLS protocol with one kind of encryption algorithm to convert packets into ciphertext, making them unreadable and seemingly meaningless - like gibberish. Only someone with the correct decryption key can access the original message, ensuring that unauthorized personnel cannot read your online data, thus, protecting the private data from leakage.
Here’s a scenario for you to understand the term Encryption clearly.
・Scenario: Ann sends a message to Bob with a VPN.
・The Original Text: Hello, Bob!
・The Encrypted Text: jdhfakfhi22o4
・Message Read by Other One: jdhfakfhi22o4
・Message Read by Bob(who has the key): Hello, Bob!
💡In specific practical cases:
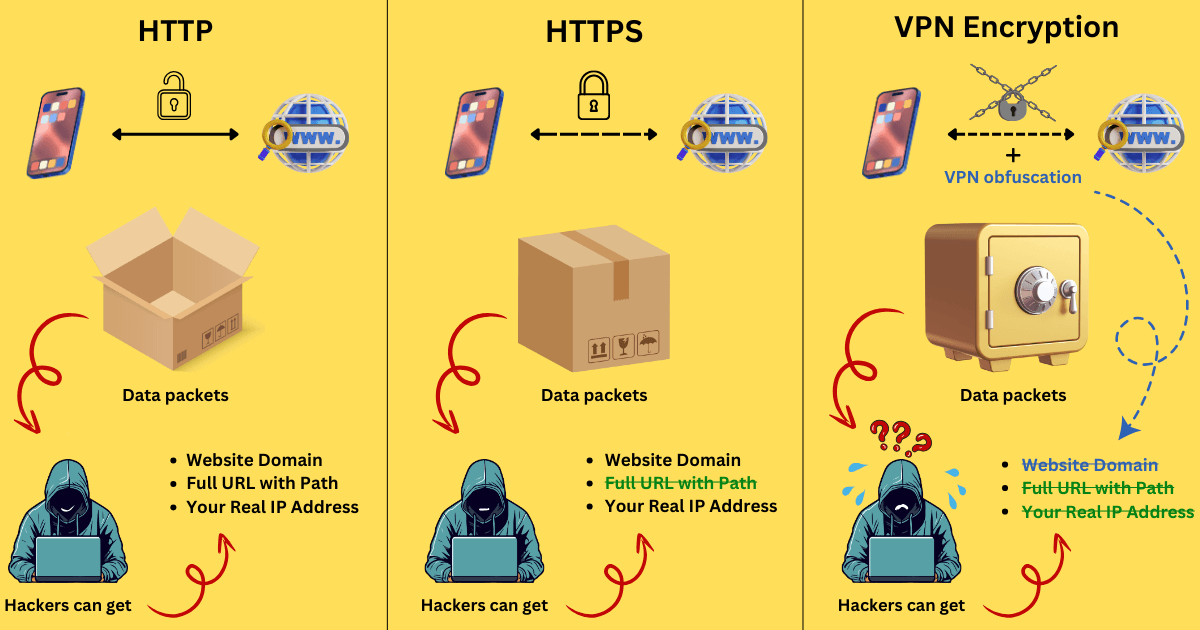
・Access Unencrypted Services: When accessing apps or websites that do not offer data encryption, like using the HTTP protocol, VPN encryption conceals the domain, the pages you visit, and your real IP address that would otherwise be exposed, preventing third parties from intercepting and viewing your data.
・Access Encrypted Services: For services that use protections such as HTTPS protocol, VPN encryption adds extra shield to app-encrypted packets, making your online data even more difficult to decrypt with two layers of TLS encryption and hiding your identity.
Attention, some reputable VPN providers, such as X-VPN, offer additional VPN obfuscation alongside encryption. This conjunction can provide further masks on the basis of data encryption, not only making your data unreadable, but also disguising it as regular traffic to provide a safer, richer online experience.
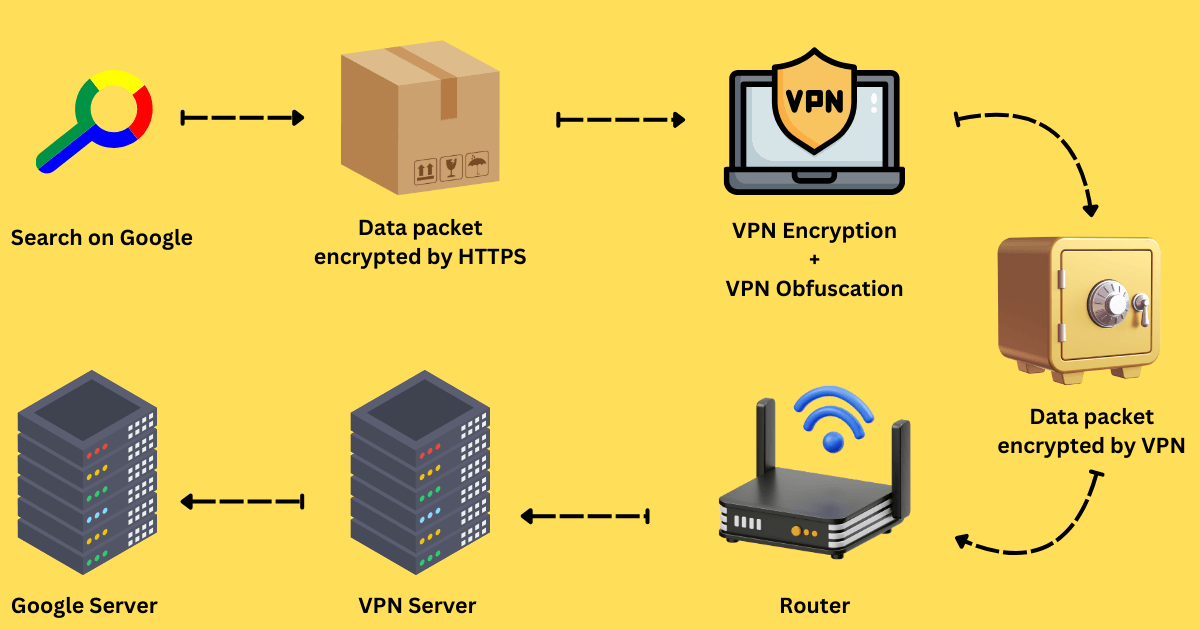
To sum up, VPN encryption is the core of VPNs, a feature that not only protects user privacy but also maintains their online anonymity.
💡You can hit the link to learn more about 30 VPN features and how to use them properly.
How Does VPN Encryption Work?
If you've already gotten a VPN, and are going to connect to a server to browse a certain webpage, the VPN encryption will work as follows.
Step 1. Send Request
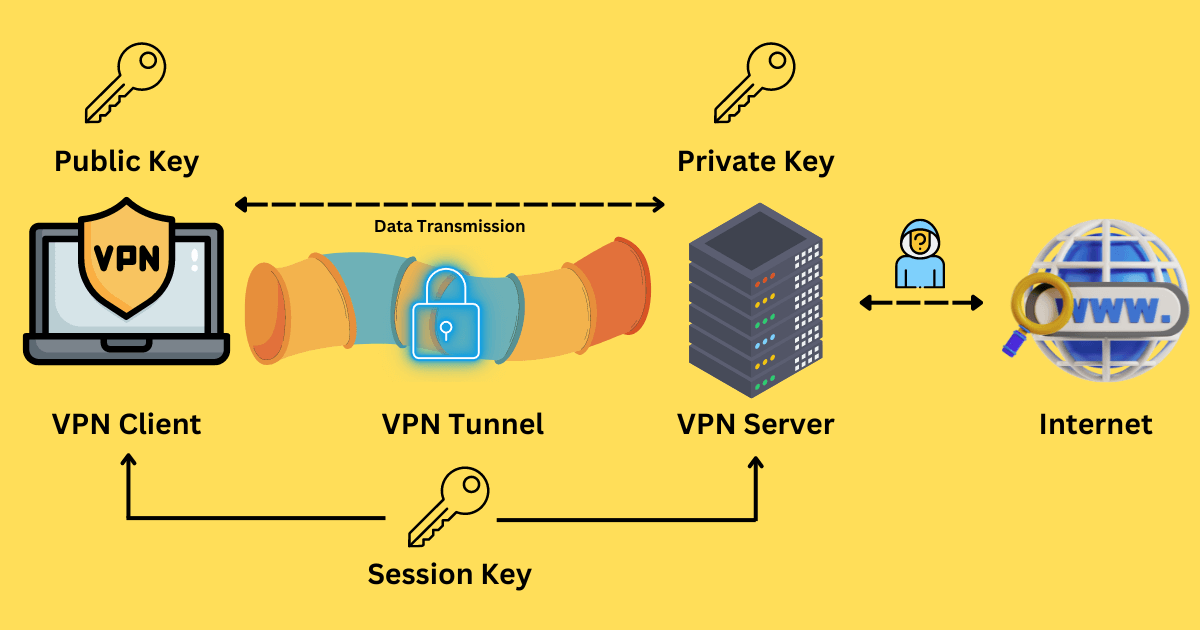
When you connect to a VPN server and perform any network activity, your request is sent to the VPN client first.
Step 2. Build a Tunnel
Upon receiving the request, the VPN service creates a secure VPN tunnel to the remote server you are connected to, preventing outsiders from viewing or tampering with the data.
Step 3. Encrypt Data
Your data is transmitted to the VPN server through this tunnel and encrypted. Here is a brief overview of the encryption process:
1. Asymmetric Key Exchange:
- The VPN client and the VPN server should do a handshake. The client sends a hello message to the server, containing its supported encryption algorithms.
- The server responds to the hello, specifies an algorithm, and sends a message to the client containing its TLS certificate (issued by a certificate authority).
- The public key of Asymmetric Key Exchange is included in the certificate sent to the client.
- Upon receiving the TLS certificate, the client verifies it with the CA to confirm the server's identity. Prevent malicious third parties from intercepting the communication.
- After the authentication, the VPN client uses the public key to encrypt data(a symmetric key), which is then sent to the VPN server.
- Then the VPN server can decrypt the symmetric key with a private key matching the public key.
2. Symmetric Encryption:
- The second phase will use symmetric encryption to create a new unique symmetric key, also called the session key.
- When the session key is established, both the VPN client and the VPN server should use this unique key to encrypt/decrypt the data during the VPN session.
3. Data Transmission
- Then the encrypted key will be sent to the VPN server with the encryption algorithm.
4. Integrity Check
- Finally, the server will use the integrity algorithm to verify that the encrypted data has not been tampered with and decrypt the symmetric key with the private key.
- Now, your data can be encrypted/decrypted by the VPN client and server via the symmetric key.
Step 4. Decrypt Data
The server decrypts the data to its original text and sends it to the intended website.
Step 5. Return Path
The VPN server encrypts data from the website and sends it through the VPN tunnel to the user's device, where the client decrypts and presents it.
The Benefits of VPN Encryption
In fact, VPN encryption is the most crucial function of a VPN, fundamentally determining the effectiveness and reliability of online protection.
Using VPN encryption, you will get the benefits from the following aspects:
・Security: The online data will be inaccessible to hackers, thus effectively blocking the online risks you may encounter, such as DDoS Attacks, scams, and phishing.
・Privacy: VPN encryption won't let third-party organizations target your surfing activities. Neither ISPs, product providers nor advertisers can access your personal info.
・Anonymity: Your IP address and network footprint will be hidden. VPN encryption will "mask" you to maintain online anonymity.
・Bypass Geo-restrictions: Encrypted traffic allows you to access geo-restricted content, such as streaming Netflix libraries from other regions or purchasing YouTube Premium at the lowest price.

Key Components of VPN Encryption
In the complete process of VPN encryption, there are 3 most important components that you need to learn about.
・Encryption Protocols - Rule Maker: Define the rules and methods for data transmission.
・Encryption Algorithms - Rule Enforcer: Perform the actual encryption/decryption according to the rule.
・Encryption Keys - Weapons of Enforcers: Provide the values for the algorithms to operate.
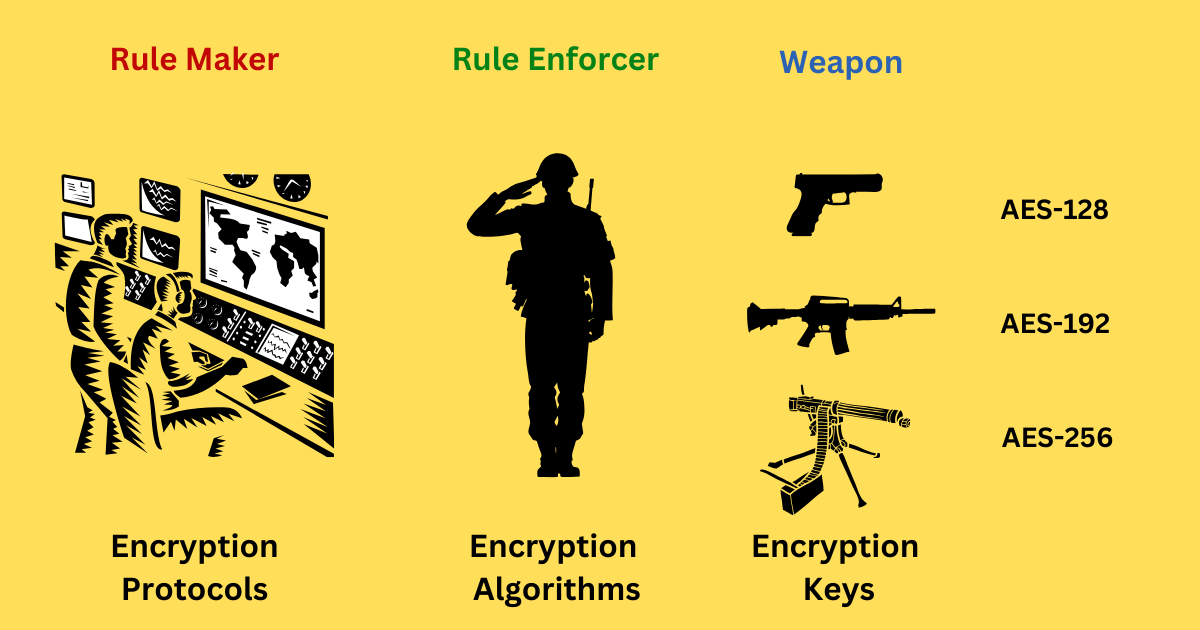
Encryption Protocols
In VPN encryption, the VPN protocol determines how the VPN should encrypt and transmit data - using different VPN protocols will result in different encryption effects.
Common VPN protocols are listed below:
・OpenVPN: Classic open-source VPN protocol, famous for robust security and reliability.
・WireGuard: The newest open-source protocol with shining speed, simplicity, and also security.
・L2TP/IPsec: Combines the L2TP protocol with IPsec, known for standout flexibility and configurability.
・IKEv2/IPsec: Has an extremely fast speed for reconnecting, very suitable for mobile devices.
💡In addition to public protocols, many lead providers have introduced VPN protocols specific to their services, such as the Everest protocol of X-VPN.
・Everest: Private protocol that has excellent unblock ability, speed, and security.
| Protocol | Encryption Ability | Speed | Unblock Ability |
| OpenVPN | ✦✦✦ | ✦✦✦ | ✦✦✦ |
| WireGuard | ✦✦✦ | ✦✦✦ | ✦✦✦ |
| L2TP/IPsec | ✦✦✦ | ✦✦✦ | ✦✦✦ |
| IKEv2/IPsec | ✦✦✦ | ✦✦✦ | ✦✦✦ |
| Everest | ✦✦✦ | ✦✦✦ | ✦✦✦ |
Encryption Algorithms
Encryption algorithms are mathematical formulas used to convert plain text into unreadable, garbled text and vice versa, ensuring that the data cannot be directly understood by unauthorized individuals.
The most highly used algorithm is the Advanced Encryption Standard, also called AES, considered as the standard for modern VPN encryption. It is known for its robust security in data encryption and transmission.
AES-256, the most secure version, encrypts data into 256-bit blocks, making it nearly impossible for hackers to decrypt via brute-force attacks due to the required computational power. This is why top VPN providers like X-VPN use AES-256 encryption.
💡Other well-known algorithms are shown below:
・ChaCha20: Well-known for its speed and security, used in new protocols like WireGuard.
・Blowfish: The oldest encryption algorithm with many many vulnerabilities.
・3DES: Enhancement of the DES algorithm, but not as safe as AES.
Different VPN protocols employ various encryption algorithms - the combination of protocols and algorithms determines the security level and effectiveness of VPN encryption.
💡Key algorithms supported by popular VPN protocols:
・OpenVPN - AES (128-bit, 192-bit, 256-bit), Blowfish
・IPsec - AES (128-bit, 192-bit, 256-bit), 3DES, Blowfish
・IKEv2/IPsec - AES (128-bit, 192-bit, 256-bit), 3DES
・WireGuard - ChaCha20
・L2TP/IPsec - AES (128-bit, 192-bit, 256-bit), 3DES
Encryption Keys
The keys in VPN encryption refer to random strings of data used in conjunction with algorithms to encrypt or decrypt online data.
Generally, the same algorithms come in different key sizes. The longer the key, the more time it takes to crack, resulting in stronger encryption. That's why even the fastest computers on Earth would take billions of years to crack AES-256.
💡Example:
・AES: Supports key sizes of 128, 192, and 256 bits.
・Blowfish: Supports variable key lengths from 32 to 448 bits.
Normally, there are 2 kinds of keys involved in VPN Encryption: Symmetric keys and Asymmetric keys. Each plays a big role in ensuring the security and integrity of VPN data transmission.
Types of VPN Encryption
Based on different key types, VPN Encryption using TSL protocol is also commonly categorized into Asymmetric Encryption and Symmetric Encryption.
Asymmetric Encryption
Asymmetric Encryption is typically used during the initial phase of VPN connection establishment (also known as the handshake).
During the handshake, asymmetric encryption has a pair of public and private keys. The sender will encrypt the data using the public key, while the receiver will decrypt the ciphertext using the private key.
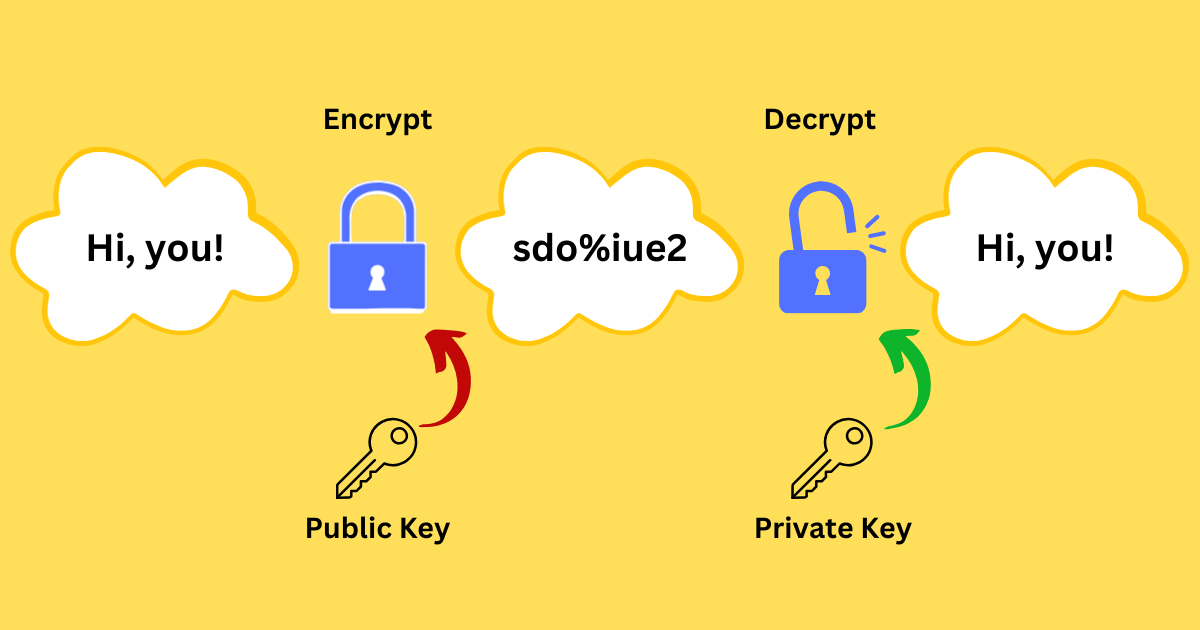
💡Here’s an example for you to understand this term clearly.
Scenario: Ann wants to send a private message to Bob.
Keys Generation:
・Bob creates a pair of keys.
・Public key: boB123
・Private key: cutebOb
Keys Distribution:
・Bob sends the public key to Ann and keeps the private key for himself.
Encryption:
・Ann creates a message to be sent: Hi, you!
・Ann encrypts the text with the public key Bob assigns to her.
・ Hi, you! ➤ sdo%iue2
Data transfer:
・Ann uses the Internet to send the ciphertext to Bob.
Decryption:
・Bob uses his private key to convert the ciphertext into the original text.
・sdo%iue2 ➤ Hi, you!
Asymmetric Encryption uses two separate keys, even if the public key is widely distributed, only the private key holder can decipher the data. This feature provides extremely reliable security for this type of VPN encryption.
However, due to its strong security, Asymmetric Encryption requires more time for mathematical operations, making it less efficient for transferring large amounts of data in VPN conversations. Thus, the time has come for Symmetric Encryption.
Symmetric Encryption
Symmetric Encryption relies on the same key for both encrypting and decrypting data, meaning both the sender and receiver must share the same key for secure communication.
Imagine it like the secret codes exchanged between spies in old espionage movies, where both parties needed to know the Morse code(symmetric key) to decode the messages.
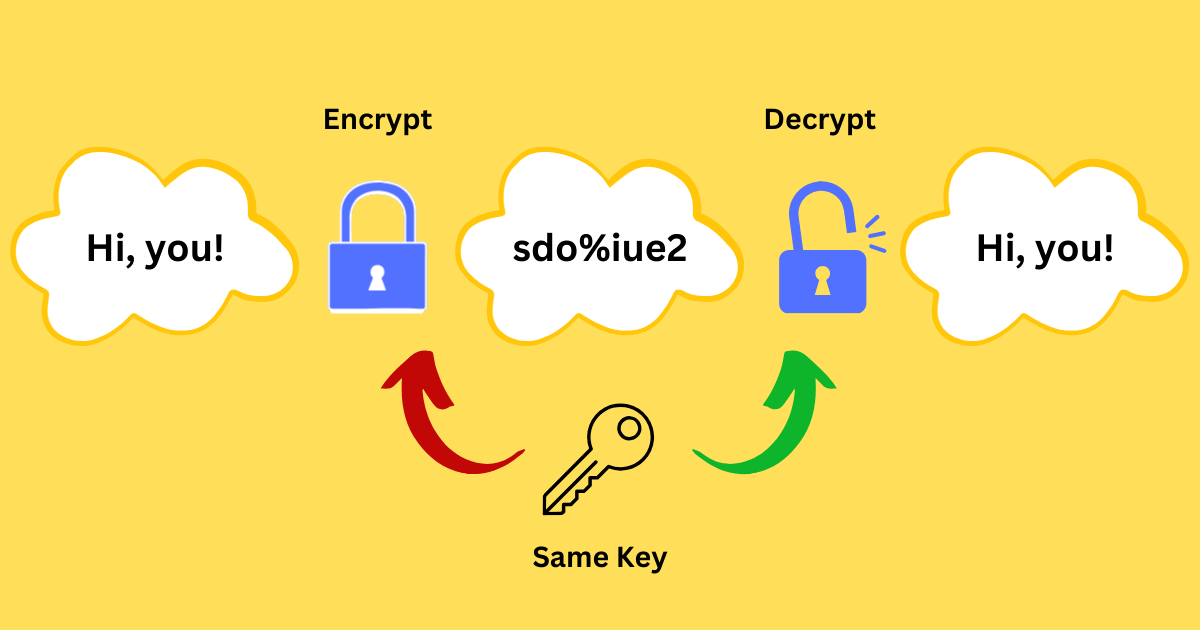
💡Here’s a vivid example.
Scenario: Ann sends intelligence she got from spying to Bob
Keys Generation:
・They agreed in advance to use a codebook named AB.
Encryption:
・Ann creates a message to be sent: Hi, you!
・Ann encrypts the text with the AB code.
・ Hi, you! ➤ sdo%iue2
Data transfer:
・Ann sends the ciphertext to Bob.
Decryption:
・Bob converts the ciphertext into the intelligence with the AB codebook.
・sdo%iue2 ➤ Hi, you!
Compared to Asymmetric Encryption, Symmetric Encryption is less difficult to compute, faster, and more efficient, making it ideal for encrypting large amounts of data.
Therefore, during VPN Encryption, Asymmetric Encryption is used to establish a secure connection, while Symmetric Encryption is responsible for the actual VPN data transfer. These two types of encryption work in tandem with each other to provide reliable security and excellent performance for VPN Encryption together.
Pro Tip: How to Test VPN Encryption?
Encryption is the absolute nucleus of VPN functionality, but as normal users, how do we know if a VPN encrypts traffic and how can we tell if a VPN product has excellent encryption capabilities?
Let’s learn how to test VPN encryption below. We will use X-VPN, the topline provider with high-level security and outstanding premium VPN features, as the demo tool. Click the button below to get a VPN download, and you can test X-VPN Encryption without an account and cost!

Check the Encryption Protocol
First, check the VPN protocol you're using. For strong encryption, opt for robust protocols like OpenVPN, WireGuard, or Everest.
Leak Tests
The primary purpose of VPN encryption is to prevent data leaks and protect your privacy from unauthorized access. Therefore, the most straightforward way to verify its effectiveness is to check whether your important data has been compromised while the VPN is active.
Check IP Leak
・Aim: Check if your real IP address is hidden.
・Tool: IPv6 Leak Test or ipleak.net.
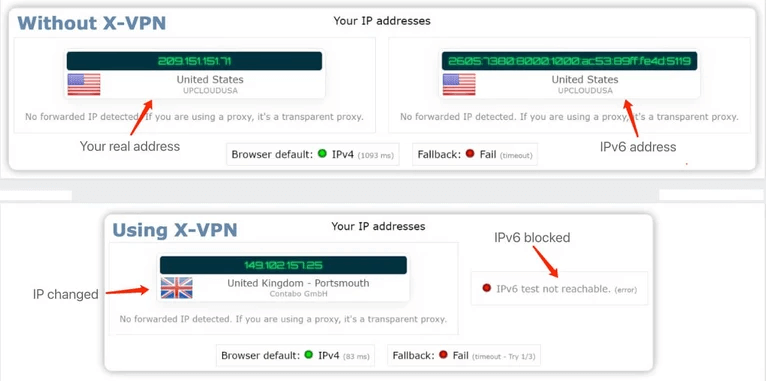
IPv6 Leak Test Results of Using X-VPN
Check DNS Leak
・Aim: Check whether a DNS leak occurred. If your DNS requests leak, the online browsing activity will be exposed.
・Tool: DNS Leak Test or dnsleaktest.com.
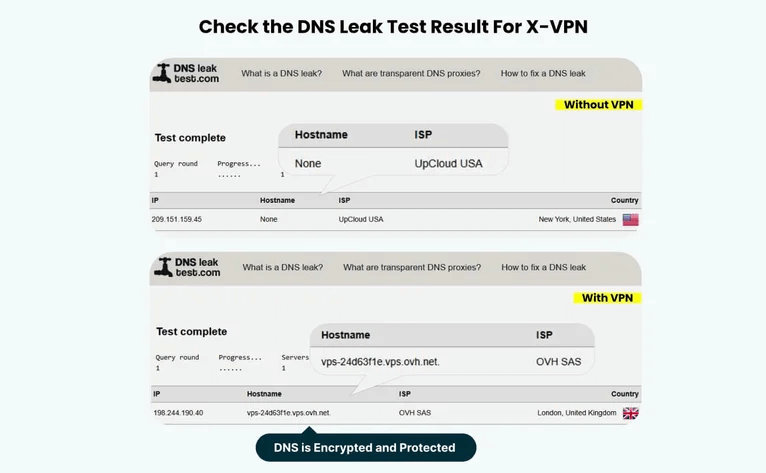
DNS Leak Test Results of Using X-VPN
Check WebRTC Leak
・Aim: Ensure any browser on your devices will not cause WebRTC leaks and reveal your real IP address.
・Tool: WebRTC Leak Test or browserleaks.com.
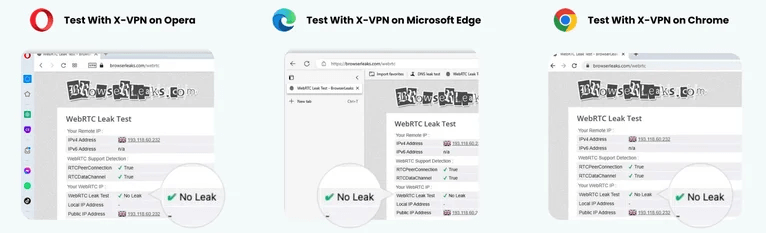
WebRTC Leak Test Results of Using X-VPN
Packet Sniffing
A packet sniffer captures network traffic, showing detailed packet information. Unencrypted data appears as readable text, while encrypted packets only display as randomly generated characters - not legible. Using the specific tool Wireshark, we can verify if VPN encryption functions correctly.
・Aim: Capture and analyze data to check whether the data is encrypted.
・Tool: Wireshark.
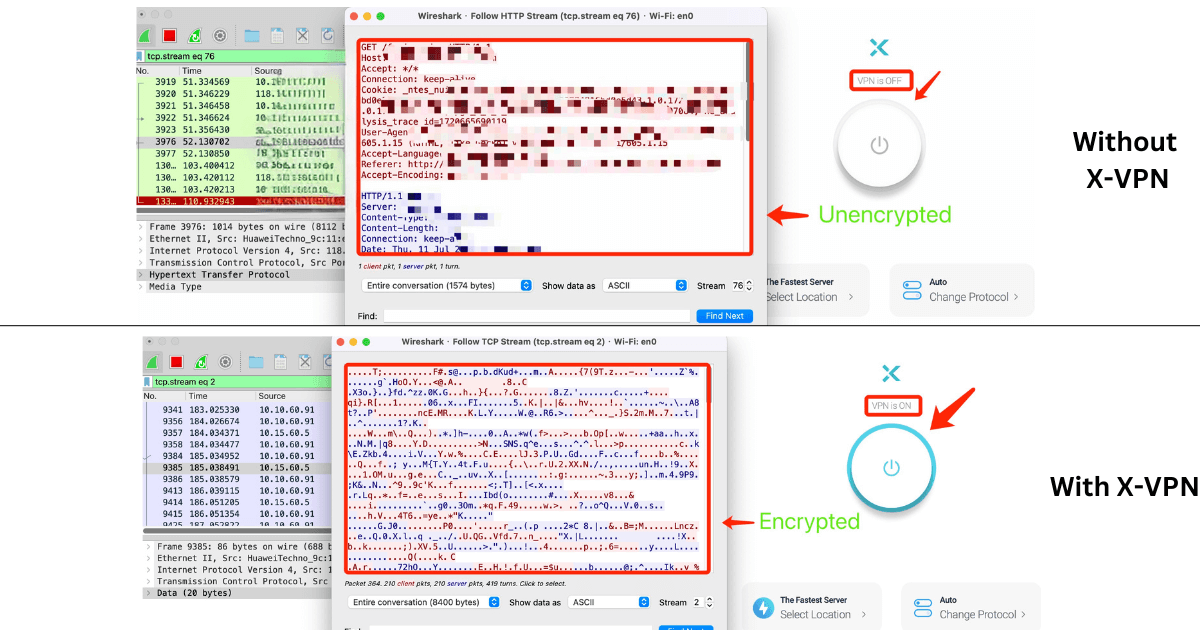
Packet Sniffing Results of Using X-VPN
By checking the encryption protocol used and running various tests, you can ensure that your VPN provides standout encryption and the superior performance you expect.
However, we have only provided you with a brief introduction to a VPN test. To learn the complete guides with detailed interpretation and tutorials, please read this blog.
Conclusion
Though VPN encryption is a highly technical and complex process, using this VPN feature is effortless. Just read this blog carefully to understand the basics, download X-VPN, connect to a server with just one click, and enjoy sturdy data encryption and other seamless online security protection.

FAQs
Does a VPN encrypt your IP?
In fact, from a technical perspective, a VPN does not encrypt your IP. But it can effectively hide your real IP address by replacing it with the IP address of the VPN server you connect to, to achieve the same “encrypt” effect. Also, it will encrypt online data to ensure your data remains private. The combination of IP masking and data encryption provided by VPNs is efficient for safeguarding surfing security.
What is the strongest encryption for VPN?
AES 256-bit encryption is currently the strongest available for VPNs. Known as the gold standard, AES is an extremely secure and unbreakable encryption algorithm. It is widely used not only in top-tier VPNs but also by government, military, and other authoritative organizations. Meanwhile, the longer the encryption key, the stronger the security, making AES-256 the most secure encryption method. Even supercomputers can't decrypt its ciphertexts within less than billions of years.
Do VPNs actually stop hackers?
Yes, VPNs do stop hackers. VPNs can enhance your online security through VPN encryption technology, making it super hard for hackers to track your online activity. Also, VPNs will mask your IP address to put on a mask for you. No one can intercept or target you - they do not even know who you actually are.
Are VPN and Encryption the same?
No, VPN and encryption are not the same. A VPN is a tool designed to safeguard surfing security and keep privacy. Think of it as an equipment suit of a police officer ready to face any threat, including bulletproof vests, helmets, handguns, handcuffs, stun batons, and even police dogs. All this equipment forms the ultimate defense against criminals, just like the encryption, split tunneling, double VPNs, kill switch, etc., from the VPN shield. In other words, VPN encryption is just one of the features that make up a VPN - just only a handgun.
Follow Us on Social Media
Recent Articles
How to Use VPNs for Secure Social Media Management
Jul 29, 2024 | 9 mins to readHow to Set Up a VPN on Windows 10/11?
Aug 14, 2024 | 7 mins to readHow to Use Signal App in Russia: Solve Signal Ban
Aug 12, 2024 | 4 mins to read30 Best FMovies Alternatives in 2024 (Still Working)
Aug 12, 2024 | 14 mins to readAccess anything anywhere anonymously with X-VPN
24/7 one-one live chat support
Ultimate protection for 5 devices
Access to all worldwide contents
8000+ servers at 225 locations
30-DAY MONEY-BACK GUARANTEE

