TCP vs UDP
What is the protocol?
When computers communicate with network devices, just as people communicate with each other, they need to use the same language to ensure smooth communication.
Rules such as how to start the communication, which language to use and how to end the communication must be determined in advance. In addition, these communication methods need to follow a rule called the protocol.
TCP/IP is the general name of various Internet-related protocols, such as TCP, UDP, IP, FTP, HTTP, and ICMP.
TCP/IP was invented in the 1970s. TCP/IP originally proposed the concept of layering, dividing complex network communication into multiple layers, each with different responsibilities, so that when a problem occurs in one layer, only the problem in that layer needs to be solved, rather than the whole thing being changed.
Significantly improve the management and maintenance of the network communication environment. The protocol has four layers, each of which is interrelated, each of which needs the support of the lower layer and supports the upper layer.
At the time, there were many other network protocols. The OSI (Open System Interconnection Reference Model) is a more unified network hierarchical protocol model. OSI referenced several protocols, such as TCP/IP, at the beginning of its design, making it relatively easy to implement the correspondence.
The OSI model has seven layers, some of which are very similar to TCP/IP:
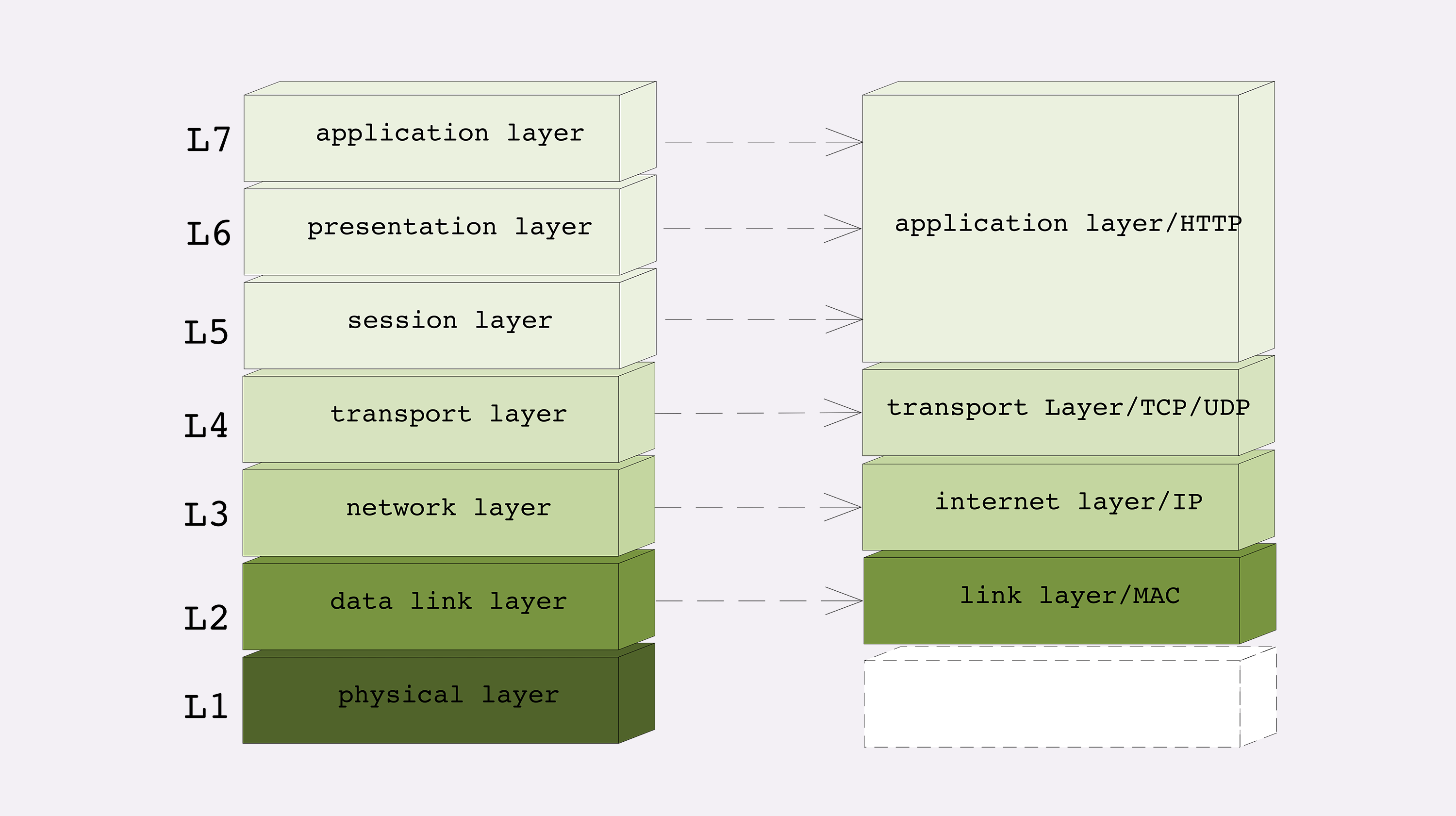
In the transport layer, two protocols, namely TCP and UDP, cannot be ignored. What are the differences between them, and how should we choose?
How does TCP work?
As we mentioned earlier, the primary purpose of protocol layering is to divide the responsibilities of each layer. For example, TCP (Transmission Control Protocol) is a transport layer protocol that allows data transmission from one digital device to another. The main task of TCP is to collect data from the application layer. Then, it divides the data into packets, assigns a number to each package, and sends the packets to the destination.
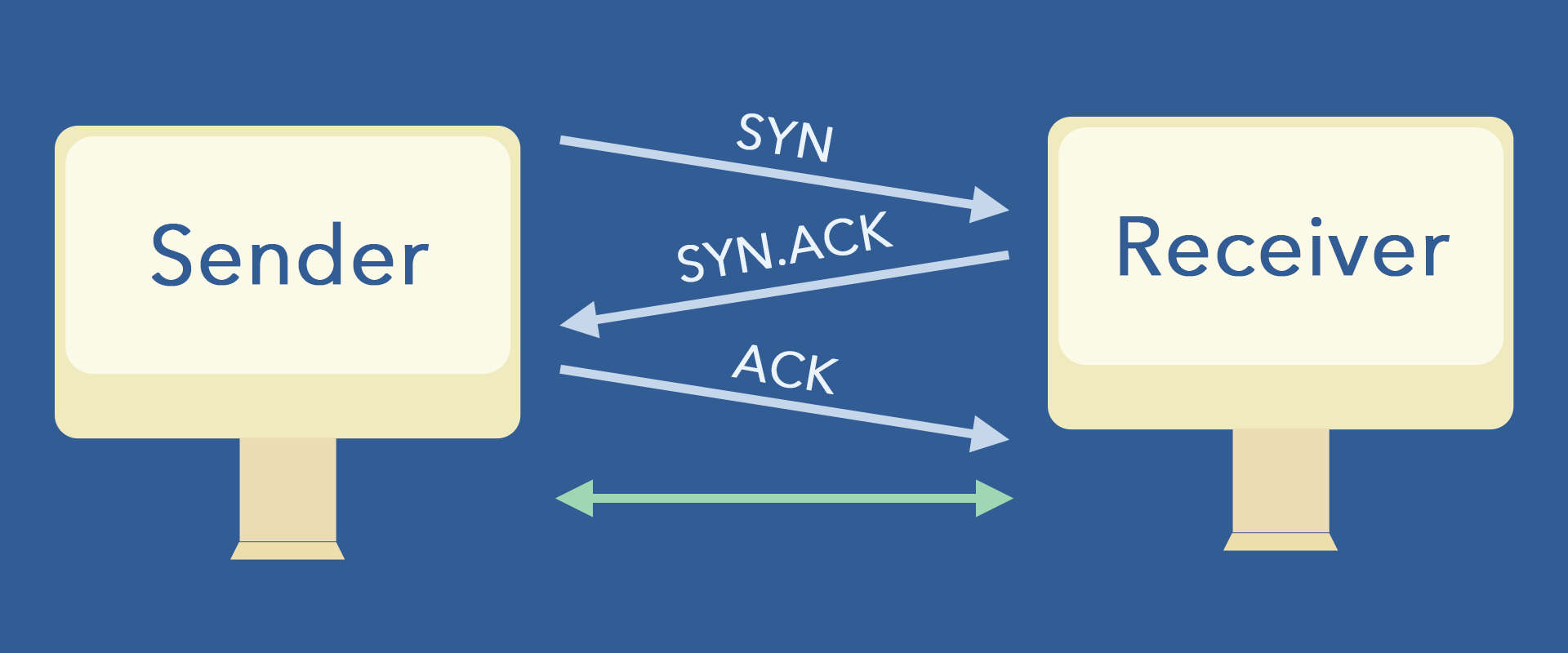
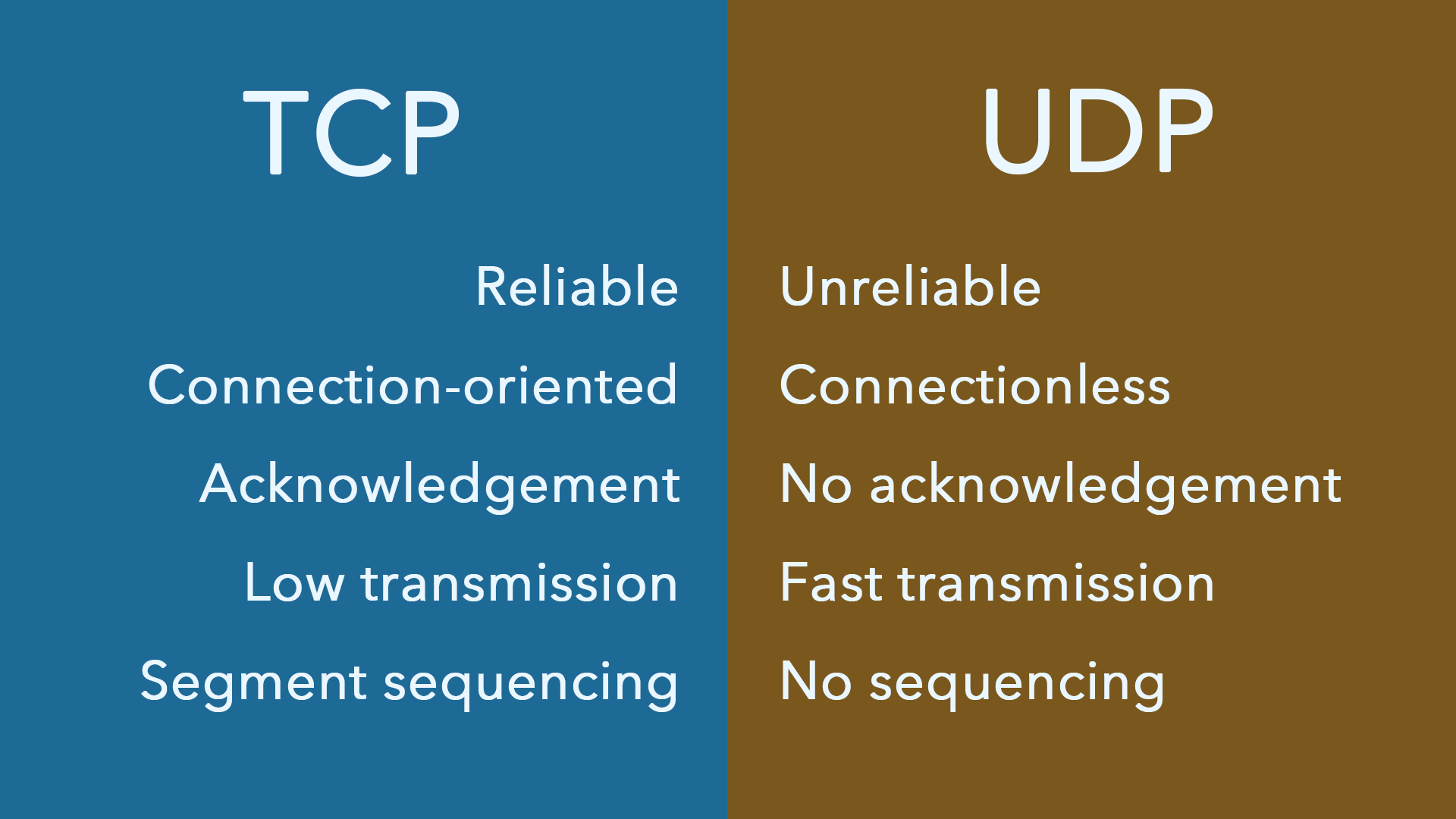
TCP is a reliable protocol. The receiver always sends the sender a confirmation message about the data packet. Meanwhile, the sender always knows whether the packet has reached another side. The request is returned if there is a failure to transfer information during the transfer process.
It reassembles packets before sending them to the application layer. Since TCP is a connection-oriented protocol, the connection is maintained until the sender and receiver have finished data transmission.
How does UDP work?
UDP (user datagram protocol) is considered an unreliable transport protocol compared to TCP's reliable protocol. Still, it provides one of the best delivery methods by using IP services to do its job.
In UDP, the receiver does not generate acknowledgement of the packet, and the sender does not wait for disclosure of the packet. It is this flaw that makes the protocol unreliable but tractable.
If acknowledgement of received data is not that important, in this case, we use UDP. It is suitable for a one-way data flow situation and is best suited for query-based communication.
UDP does not guarantee that packets are sent sequentially. It is stateless and does not provide any congestion control mechanism.
What are the differences between TCP and UDP?
We can see the differences between TCP/UDP from these aspects:
Connectivity
TCP is a connection-oriented protocol. Since we use this protocol in conjunction with the IP protocol, it is generally called TCP/IP.
Sending and receiving data must establish a reliable connection between the two parties. 3 "handshakes" to establish the relationship, 4 "waves" to disconnect the connection, laying a reliable foundation for data transmission.
A good connection has been established before the data transmission starts, and the receiver will accept the data packets in an orderly manner to ensure the accuracy of the data.
UDP is a connectionless protocol. Before data transmission, the data sender and receiver do not establish a connection. Instead, the sender transmits data to the network faster, and the receiver reads message segments from the message queue. Since the sender and receiver do not have a good connection, the receiver receives packets out of order.
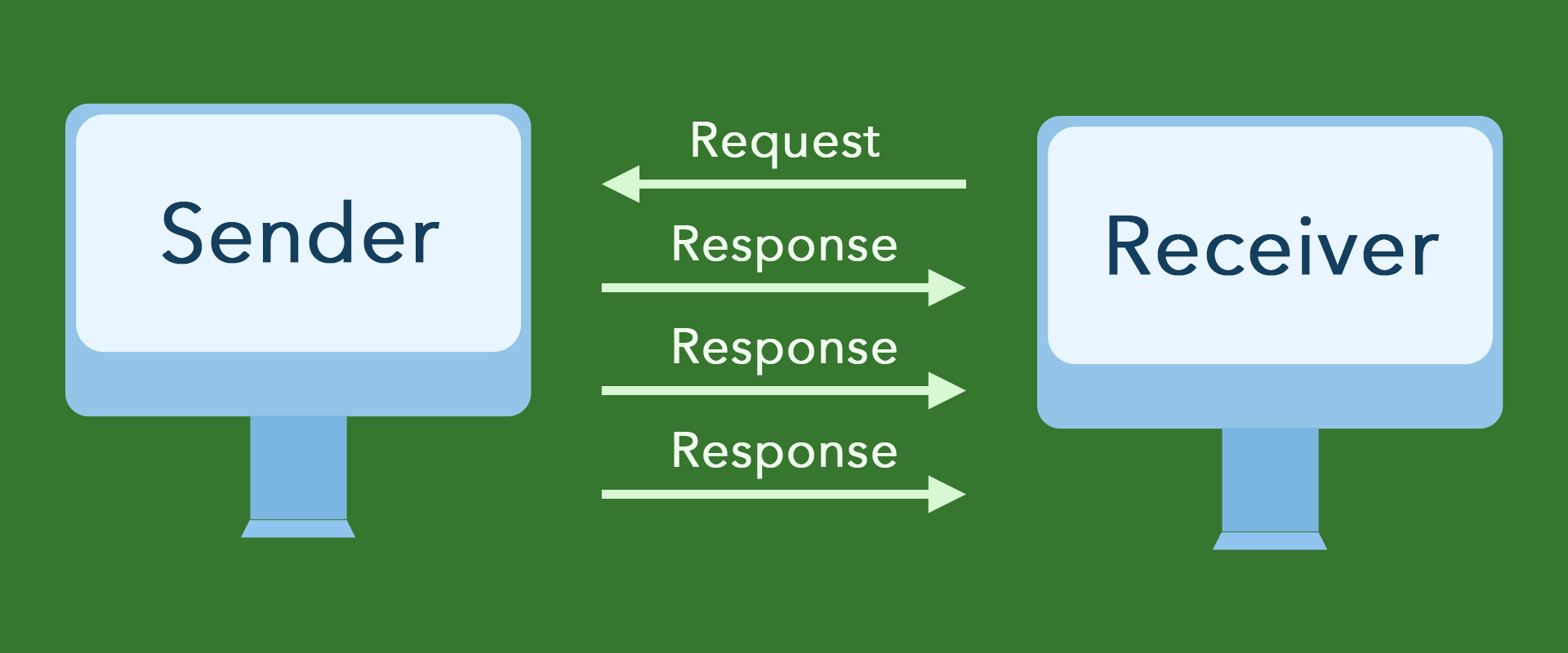
Reliability
TCP provides reliable transport services, ensuring the reliability and order of data reception. Many methods are used in the transmission process to ensure reliable transmission services on the connection, such as numbering and acknowledgment, flow control, timers, etc., to ensure that data is error-free, lost, repeated, and arrives in sequence. If the transmission fails, it will request a retransmission.
UDP does not guarantee reliable delivery during delivery. Instead, it relies on higher-layer protocols to ensure reliability. Disordered, non-accurate transmission methods are more suitable for some requirements that do not require high data corruption.
How to choose TCP and UDP?
Due to the advantages and disadvantages of the TCP and UDP protocols, we can choose the more suitable protocol to meet different needs.
The TCP protocol is reliable, adding complex mechanisms such as checksum, serial number identification, sliding window, confirmation response, congestion control, etc., establishing a tedious handshake process, and increasing the consumption of system resources by TCP. Therefore, there is a particular delay effect on data transmission, reducing transmission efficiency.
TCP is suitable for typical applications that require low transmission efficiency but high accuracy, such as the HTTPS (Hypertext Transfer Protocol Secure), HTTP (Hypertext Transfer Protocol), SMTP (Simple Mail Transfer Protocol), and FTP (File Transfer Protocol), etc.
UDP is connectionless, has unreliable transmission, data delivery as soon as possible, simple protocol, fewer resource requirements, fast transmission speed, and high real-time performance. Therefore, it is suitable for typical applications requiring high transmission efficiency but low accuracy. It is used for video streaming, video telephony, voice over IP services (Internet calls), DNS (Domain Name System), etc.
Follow Us on Social Media
Recent Articles
How to Use VPNs for Secure Social Media Management
Jul 29, 2024 | 9 mins to readHow to Set Up a VPN on Windows 10/11?
Aug 14, 2024 | 7 mins to readHow to Use Signal App in Russia: Solve Signal Ban
Aug 12, 2024 | 4 mins to read30 Best FMovies Alternatives in 2024 (Still Working)
Aug 12, 2024 | 14 mins to readAccess anything anywhere anonymously with X-VPN
24/7 one-one live chat support
Ultimate protection for 5 devices
Access to all worldwide contents
8000+ servers at 225 locations
30-DAY MONEY-BACK GUARANTEE

