VPN Protocols
What are VPN protocols?
VPN protocols are rules that determine how VPNs encrypt and transmit data. They provide VPN users with a stable and secure connection.
How do VPN protocols work?
VPN protocols establishes secured and encrypted connections between your device and the VPN server in this process:
1. Encryption: Once connected, VPN encrypts your data according to the selected protocol, making your data unreadable to intruders.
2. Secure Tunneling: Encrypted data will be transferred to the VPN server through a secure digital tunnel. This secure tunnel conceals your IP during data transmission, enabling anonymous internet access.
3. Authentication: VPN protocols will confirm that your device is connecting to a legitimate VPN server, enhancing security.
Types of VPN protocols
There are several types of VPN protocols, offering different encrypting method. While there are common public VPN protocols, some VPN providers have developed their own private VPN protocols.
Common VPN protocol types
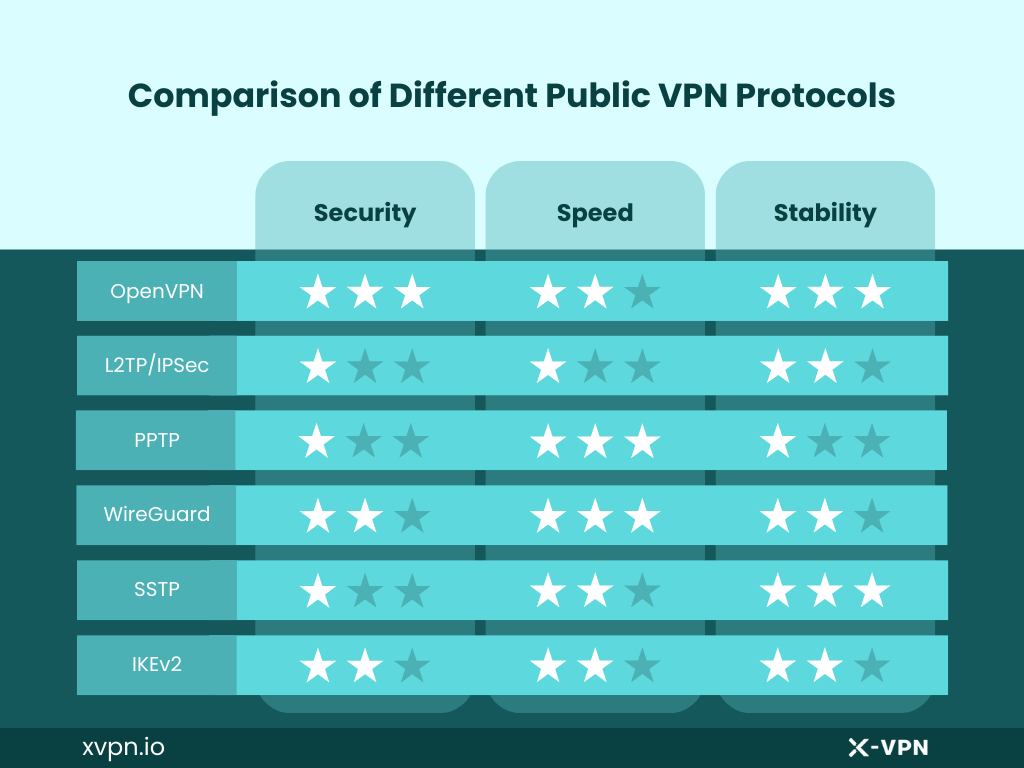
1. OpenVPN: an open source VPN protocol. It uses AES 256-bit encryption and adaptable to most platforms.
2. L2TP/IPsec: L2TP stands for Layer 2 Tunneling Protocol, while IPSec stands for Inter Protocol security. Used together, L2TP/IPSec offers more security and is very flexible as well.
3. PPTP: PPTP, or Point-to-Point Tunneling Protocol, is one of the earliest VPN protocols developed by Microsoft, offering high speed, but low security standards.
4. WireGuard: WireGuard is a fast and secure protocol developed for modern cryptographic and security requirements. It is fast and efficient while ensuring secure communication.
5. SSTP: Secure Socket Tunneling Protocol was developed by Microsoft, and is commonly supported by Windows. It works by creating a secure tunnel over SSL/TLS encryption.
6. IKEv2: Stands for Internet Key Exchange Version 2. It reconnects fast, and performs well on mobile devices, but may be blocked by firewalls.
Private VPN protocols
1. NordLynx: NordVPN has developed this protocol based on the WireGuard protocol. While offering fast connection, NordLynx ensures more security and anonymity.
2. Lightway: Lightway is an open-source protocol developed by ExpressVPN entirely in house. It uses sleeker code, which means it can ran faster and is easier to develop additional features.
3. Everest: Combining security and anti-blocking capabilities, X-VPN develops Everest protocol for fair access to VPN services. It employs AES-256 encryption and uses various transmittion protocols. Meanwhile, Everest Protocol offers entire obfuscation, making VPN usage more difficult to detect.
FAQ
1. How do VPN protocols differ from each other?
Each protocol employs unique encryption and data transmitting, influencing speed, stability, and security levels.
2. How to choose the best VPN protocol?
Choosing the right VPN protocol depends on the specific needs of the situation, as different protocols have different strengths and are suitable for different scenarios.